A Board member, a CEO, and the CIO from the same company walk into a bar filled with their closest suppliers and vendors. Each of you has a draft copy of the next annual report, a hard drive, and a poodle under your arms. What compromise presents the most risk to your business? How much will the tab cost at the end of the night?

ANSWER: Your suppliers and vendors… Standing there among your closest suppliers are some who inadvertently threaten your company. Why? Because their IT networks have been, are, or will be compromised, and that means so will you…
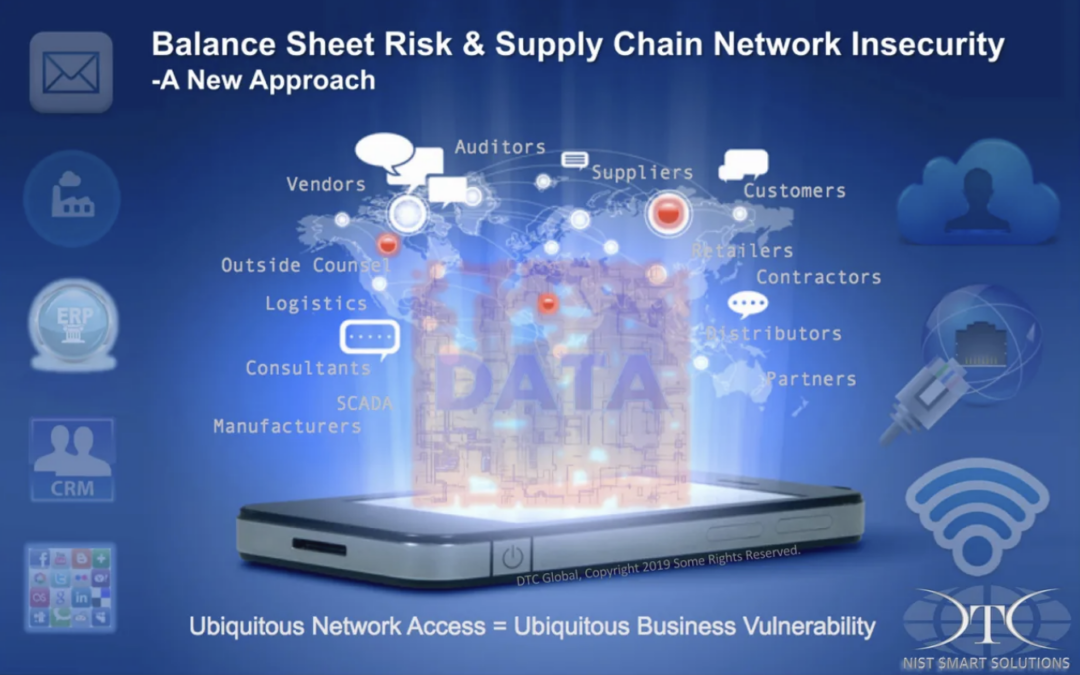
Your company is dependent on interacting with hundreds, or perhaps thousands of “trusted” third-party networks every day. In a bar full of friends and colleagues, one might be able to trust them with your poodle, even your next annual report, but the likelihood that the thousands of devices directly and indirectly communicating across your corporate network are, or will be compromised is a statistical certainty. The business risk begins with determined criminals knowing your supply chain represents a vast and vulnerable attack surface. The intentional compromise of one of your suppliers makes it just a matter of time until your network is penetrated and exploited. How would your top-rated IT staff defend against a spear phishing email from a person whom you interact with every day, sending you a familiar link to a weekly report, which is actually a malicious exploit hidden on your supplier’s server that will cost your company millions of dollars until the compromise is discovered some time in 2017?
YOUR balance sheet is at risk because your business is at risk.
Your next annual report and your ability to keep YOUR DATA, YOURS…
is dependent on your supplier and vendor IT networks remaining secure.
A new approach is required…
Original article HERE
This article was originally Published on April 7, 2016, Linkedin
Recent Comments