IMPORTANT:If these practices aren’t being done on a regular basis within your organization, you’re not compliant, and it’s time to take action.
There is no shortage of articles out there about CMMC/NIST 800-171, and what it means to contractors. These are great articles and the subject matter is both valuable and necessary, but my goal is to start to break down some of the broad stroke data to usable, actionable steps to guide those actually implementing the CUI requirements and NIST standards. Let’s start with media protection, marking, and labeling devices. CUIsupply.com is the vendor we use for CUI marking labels and other useful supplies. So let’s get back to the basics, and review the things you can do to move your business toward CUI compliance.

This article will not cover all the requirements, there are VERY specific requirements for specified categories of CUI like Export Controlled information (EXPT) that must be followed, but this will start you down the path.
IMPORTANT: If these practices aren’t being done on a regular basis within your organization, you’re not compliant, and it’s time to take action.

Many well-intentioned companies are still waiting on updated DoD guidance on marking expected in the DoDM5200.01 vol. 5 to take action. As DoD continues to update their manual, the guidance to properly mark CUI is already issued by the CUI Registry. By Federal Regulation, companies can expect DoD’s marking guidance on CUI to reflect the current guidance. By Federal Regulation, the DoD may enhance the requirements, but may not reduce them or alter them. Legacy markings identified in DoDM5200.01 vol. 4 are prohibited to use by 32 CFR, part 2002. If you don’t know the details within this section of the Code of Federal Regulations, you need to read it VERY carefully.
Follow specific marking instructions. https://www.archives.gov/files/cui/20161206-cui-marking-handbook-v1-1.pdf

UNMARKED CUI and Marking Responsibilities for Industry: Mythology vs. Reality
There’s a great deal of mythology surrounding unmarked CUI, so we need to look to the regulation for guidance to develop strategies to meet the requirements AND safeguard CUI. Everyone recognizes the government’s responsibility and challenges in marking ALL CUI within their contracts. Contracting Officers are acquisition professionals, not CUI subject matter experts concerning CUI-related regulations, agency policies, specific technical details of the contract, or even knowledgeable of the confusion across industry as we struggle to meet the requirements. The USG program managers focus on special sensitive areas of their technologies to protect and rely on the existing regulatory definitions to encompass “all” the details not possible to capture in every contract. [Everyone would agree USG contracts are complicated enough already].
EAR and ITAR export control requirements are useful reference already in practice concerning CUI. USG officials responsible (DDTC/BIS) for enforcement and Export Control practitioners have a long history of navigating “classification jurisdiction and determination”, which is a complicated process for deciding “what is and is not ITAR/EAR controlled”. This process is difficult and requires significant expertise and the process has far too much ambiguity and room for error/misinterpretation by all parties. For CUI categories outside of the complications unique to ITAR and EAR requirements and the requirements for properly marking CUI//SP-Export Control, Government and industry can simply review the definitions of technical information and Controlled Technical Information (CTI) directly within DFARS 252.204-7009(a) Definitions and then reference the CUI Registry. It is far simpler to identify and designate CUI Basic and other specified categories such as Controlled Technical Information (CTI). The resistance is rooted in the reality, those definitions encompass a great deal of technical documentation. The broad definitions were purposeful, because they were meant to safeguard as much of the USG technical information as possible. For now, we must work within the constraints of the definitions and the regulations.
The bottom line- If the information a company or individual receives or creates in accordance with their USG contracted responsibilities, and the information meets the definition of any category of basic or specified CUI, it must be treated as CUI, handled as CUI, and meet the full requirements detailed within 32 CFR, part 2002.
Below are Three Foundational “Realities” critical to identifying, marking, and handling CUI in accordance with the current requirements.
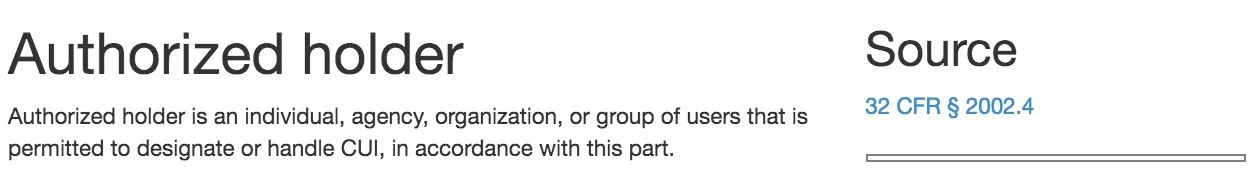
#1 Your company and the individuals within your company are “Authorized holders” of CUI if you meet this definition.
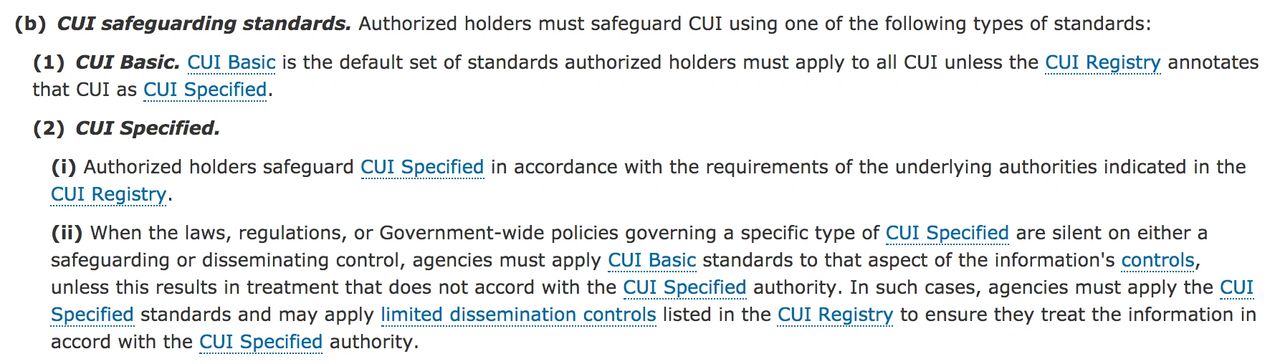
#2 The authorized holder bears the responsibility for abiding by the handling requirements regardless of whether the CUI is properly marked or not.

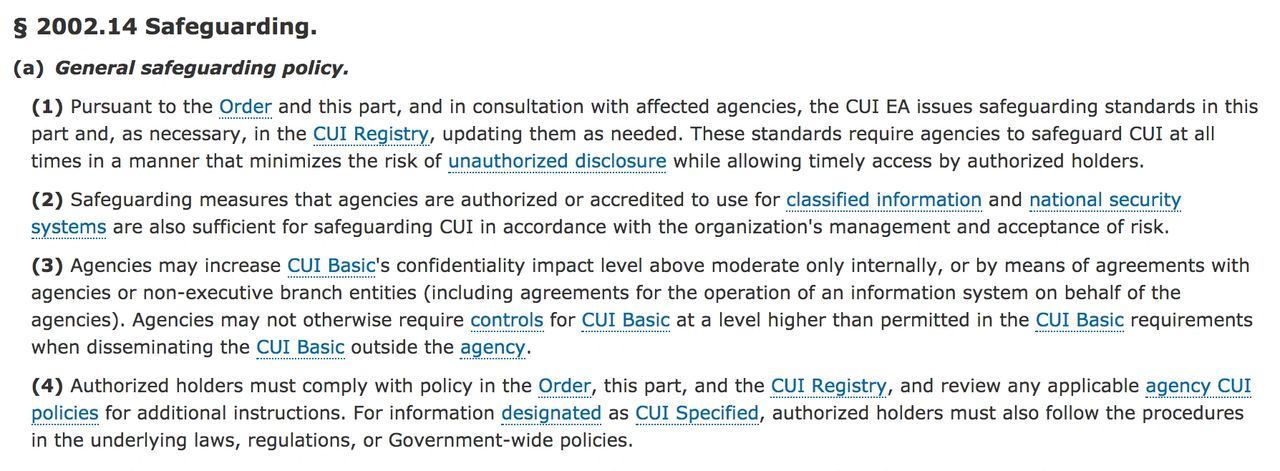
#3 For non- Federal Information systems, according to 32 CFR, part 2002 (below) Basic and Specified CUI must be protected by NIST 800-171 requirements.

Redacting CUI and descoping a document that is already marked as CUI are tricky areas to navigate with no clear guidance and beyond the scope of this article. More about that in another blog post later.
Now, let’s start with discussing media protection from a NIST 800-171 standpoint? DoD contractors and suppliers like every other business use flash drives, CD ROM’s, external hard drives, paper, computers, etc. in their daily operations. When a contractor uses that media to display, store, archive, or create Controlled Unclassified Information (CUI), by Federal Regulation it must be properly marked and identified in accordance with the marking guidance within the CUI Registry.
Once a digital removable device contains CUI you must:
· Label it: All devices that have CUI on them (at any time) must be labeled with “CUI” or “Controlled” and your business name. The CUI must be secured with one barrier of protection from unauthorized access when not in use, such as a properly labeled storage cabinet. Areas and rooms containing CUI must be properly signed to acknowledge the presence of CUI and for determination the access for those authorized or unauthorized.
· Buying Labels: If you’re in government, GSA has a 60 day wait for any CUI labels. The only current company making CUI marking labels is CUIsupply.com – We direct all our clients there. In some cases, they have improved the standard forms consistent with CUI marking guidance for commercial environments. Our customers have found them to be very valuable in media and document management. Standard Form 902– computer, cd, external hard drive labels. Standard form 903 – Flash drive labels. Form 904 – locking cabinet or label for boxes locked in storage.

· Lock it up. Digital storage devices (USB, external hard drives, etc.) must be controlled and issued in a media library (locked cabinet, drawer, etc).
· Encrypt it. CUI at rest on a removable media device must be encrypted.
· Check it out. Any device coming out of the media library must be “CONTROLLED” on a tracking list so the company knows, who has it, what type of CUI it contains, where to find it, and the person must be qualified, trained on the responsibilities and authorized to handle CUI.

· Keep it in your control. If you are not using, it must be secure. Lock it up. If you leave your workspace or there are people in your work area who are not authorized, lock it up. Don’t forget the clear desk policy!
Printed documents containing CUI:
· Get it. Immediately get it from the printer in a secure area.
· Cover it. This is not a requirement but highly recommended by 32 CFR 2002. SF 901 is a coversheet to conceal the CUI that may be on a document front or is some cases, the back.
CUIsupply.com has cover sheets probably less expensive than you can print them.
· Mark it. In some cases, CUI is not always marked but you are still responsible for the document status or your company may have created the CUI document in the design process. Marking accurately is complicated and cannot be explained in this article but must be done. Example would be CUI//SP-EXPT or CUI//SP-CTI. You can use the archive.gov article referenced above.
CUIsupply.com has marking stickers to easily identify your documents.
· Lock it up. If you are not using it, lock it up. If you leave your workstation or people who are not authorized are around, lock it up.
Getting rid of it. Your building should have locking disposal containers for securing CUI in until it can be destroyed properly. See your company policy on CUI destruction and disposal.

Label computers and network devices containing CUI:
· Identify it. Be labeled if they are used to store of process CUI. Use a SF 902 sticker.
· Foreign Travel. You should never conduct foreign travel with your computer that contains CUI unless it is specifically authorized and also configured by your IT department to travel. Some CUI, such as Export Controlled information (EXPT) must be specifically licensed to be carried out of the United States. KNOW THE REQUIREMENTS.
· Protect it. Do not attach a non-compliant devices to your CUI compliant computer. There specific computer vulnerabilities that are designed to be transmitted from device to device. Example- Charging your personal cell phone from a USB port on your computer.
Media protection in transit must:
· Be specifically approved.Removable media and paper containing CUI should not be taken off premises without specific authorization and training.
· Must be encrypted. Electronic data must be encrypted for travel or transmission.
· Lock it up. If CUI data is not in your possession it must be locked up and out of sight.


I’m interested in understanding your interpretation “Mark media with necessary CUI markings and distribution limitations”.
Media vs a laptop. Do we mark laptops, seems like a bad thing to do. We are told not to mark anything we mail on the external envelope. I would think a laptop should be treated the same.
Please email me your thoughts.
CUI Notice 2019-1 provides mandatory guidance for agencies. DoDi 5200.48 applies CUI EA guidance including CUI Notice 2019-1 to all DoD personnel under DFARS 252-204-7012. (See references section). NIST SP 800-171 control, MP 3.8.4 et al.
Marking and labeling of devices processing, transmitting, and storing CUI is a required application of the requirement, not an interpretation of the requirement. Consistent with NARA CUI Marking Guidance and CUI Notices the device is a container for CUI, just as a cabinet or room. Specific DoD marking guidance is not necessary because the guidance is already provided by the CUI EA. DoD Mandatory CUI training, CDSE provides this guidance in the training as well.