Aero-Glenn was the first small company to successfully complete their DoD DIBCAC High Assessment under the DoD’s joint voluntary assessment program.
Aero-Glenn used CMMC ePU Implementation Guidance to succeed. The 12 steps below are extracted from the same implementation guidance to provide certainty for everyone on their journey towards CMMC certification. Together, we can secure American’s Defense Supply Chain.

Expected to be awarded in 2023 by DoD, no company is certified yet.
Success means that the CMMC interim rule expected early next year should provide the details and authority for those companies like Aero-Glenn who worked diligently, volunteered, and met the requirements during the voluntary program to be authorized to certify. With reliable guidance, they have proven this can be done with a modest budget, two years of sweat equity, and limited external assistance. To say the least, they are not your average IT team, but we are moving closer to “bullet-proofing” a path to certification. Know-Do-Certify is the goal we are relentlessly striving to meet. You don’t have 24 months.
A very important disclaimer is that “qualified” doesn’t yet mean certified… The DoD has no control over the final wording of the interim rule. The milestone is SIGNIFICANT. Aero-Glenn is a 75 person tier supplier to Bell Helicopter deserves tremendous praise for their hard effort, sweat equity, and performance. The DoD DIBCAC team led and provided oversight of Aero-Glen’s assessment. The Texas MEP (TMAC) provided direct support to Aero-Glenn and was present during the assessment. Since 2019, far greater than 10,000 hours has been invested in developing definitive implementation guidance and reference documentation to provide clarity and certainty for the CMMC ecosystem to do the work necessary to certify at the lowest cost possible with confidence. Aero-Glenn used this CMMC ePU documentation supported by the Texas MEP to succeed.
In order for companies to satisfy CMMC certification requirements they must understand CMMC controls and practices with clarity and certainty. Our goal is to provide that certainty in order to lower the cost, risk, and involvement of the fewest possible external resources possible needed to certify…at a scale that is likely to exceed all expectations. Safeguarding CUI is the primary focus of CMMC and failure is not an option.

-
Improve clarity
-
Improve certainty
-
Reduce risk
-
Reduce cost
-
Develop common industry guidance for A WAY, NOT THE ONLY WAY to certify.
Companies that understand and address the DFARS clause, NIST SP 800-171 controls or CMMC practices then do the work… will win. There are no shortcuts, no winks, and no mulligans. Only results matter.
I hope your company wins BIG and that you see DFARS 252.204-7012 and CMMC certification as the greatest opportunity to expand your company’s market share in a generation. Despite the hundreds of hours of free webinars, training, and warnings…many will continue to ignore the inevitable. It’s time for your company to win.
Only NIST SP 800-171 and DoD have the statutory and regulatory authority to provide the official references for your efforts, but they have decided not to provide the “how” which guides the implementation of their requirements. There are NUMEROUS obscure references that are needed to best understand the how. Think of CMMC ePU as a fully referenced and cited “cliff notes” for all those references with step by step guidance and evidence. Templates are NOT useful, because there are very few people who know accurately what would go in the blank spaces. So, CMMC ePU provides a “a way” to implement with confidence using the implementation guidance. This is the critical enabler that can help you successfully navigate “the way” you need to do it unique to your environment and win.

Most of your competitors maybe not aware of the challenges before them. They may “think” they know or are hoping to “figure it out”. The data indicates that most are struggling, even more sophisticated companies with bigger budgets. It’s going to be a very, very expensive series of lessons for many in the Defense Industrial Base.
These expensive lessons you can avoid. We highly recommend carefully reviewing the data below and choosing a better plan.
What are the facts about DoD’s CMMC-related assessments and what do they tell us?
During 2021-22, the estimated failure rate of 300+ companies seeking the authority to certify the DIB as C3PAO’s was +90%. Only two companies were indicated by reliable sources to successfully complete their assessments of the initial four under the joint voluntary assessments. This echoes the DIBCAC’s SPRS score and survey analysis during the CMMC Town Hall several months ago. Many have been working very hard in the CMMC ecosystem over the last three years to address these concerns.
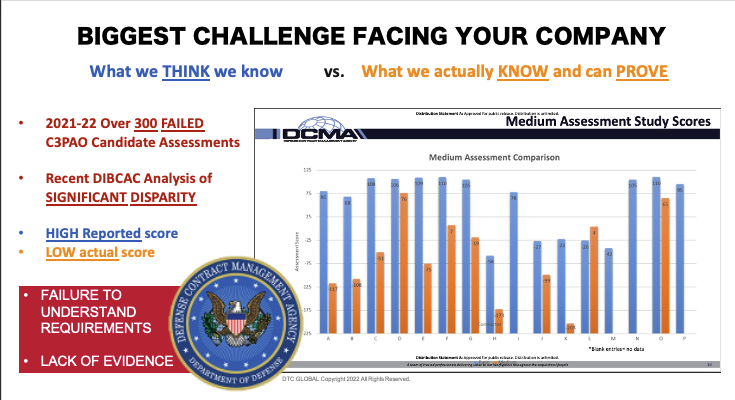
DoD personnel stated two primary reasons they failed to certify:
- They did not understand the requirements
- They did not have sufficient evidence to meet the requirements.
12 Steps Towards CMMC Certification
Below is a modified Table 2 directly from CMMC ePU guidance. Remember, this guidance provides general steps as part of a much larger set of detailed guidance. We hope it helps you navigate your path towards certification. We have a few available slots within a 65 hour Small Business DIY cohort pilot program in January and February that can SIGNIFICANTLY REDUCE the cost to prepare, train, and fully document your company in order to meet the minimum DFARS 7012 and SPRS requirements as you implement tasks on your POA&M. If you are interested in participating, please contact [email protected] Certain qualifications and exclusions apply.
CMMC ePU Implementation Guidance, Table 2 – General steps for implementing each CUI Security Control/CMMC Practice.These steps are common to the implementation of all NIST SP 800-171 requirements CMMC Practices. Follow these general steps to keep you on track. Know-Do-Certify. Remember, there are NO SHORTCUTS. Definition – (CUI) Security Controls and Controls are safeguards or countermeasures prescribed for an information system or an organization to protect the confidentiality of the system processing, storing, or transmitting CUI. CUI Security controls are the safeguards or countermeasures organizations implement to satisfy (CUI) security requirements. The management, operational, and technical controls (i.e., safeguards or countermeasures) prescribed for an information system to protect the confidentiality of the system and its information. (NIST SP 800-171, Adapted for use) |
| Step 1. CUI Discovery: Understand the specifications for each Basic/Specified CUI security requirement that apply to each CUI Security Control (NIST) or CMMC Practice and all assessment objectives CUI security domain (network that contains CUI/FCI).
The specifications are highlighted below in CMMC ePU Implementation Guidance, Table 2. for each CUI security control and CMMC Practice are ALREADY included within CMMC ePU implementation guidance. Check to make sure those specifications match YOUR categories of CUI. About 60% of DIB companies have Export Controlled information within your environment.See Sensitive Data Governance Policy. |
| Step 2. CUI Discovery: Identity, determine, and mark (designate) the CUI/FCI (in any form) received, processed, developed, transmitted, secured, stored, and disseminated (internally/externally) during the contract performance. (32 CFR 2002.4t; DoDi 5200.48)
Wherever the CUI/FCI flows, the CUI security control (NIST) or CMMC practice must be applied. Ensure the entire CUI lifecycle is accounted for CUI/FCI in any form and devices/media processing, storing, or transmitting CUI in each procedure including sharing and destroying CUI physical/digital in devices/media/other forms. See DCSA Quick Start Guide for Industry. See Sensitive Data Governance. |
| Step 3. CUI Discovery: Understand and develop a plan to align the Business & IT environment with the flow of CUI/FCI necessary to satisfy and meet all appropriated Basic/Specified CUI security requirements during contract performance.
CMMC ePU Policies include a pre-written, researched, comprehensive and accurate CUI/FCI Sensitive Data Governance Policy written to guide this process. See Sensitive Data Governance Policy |
| Step 4. CUI Discovery: Identify and develop a plan to apply the Basic/Specified CUI security requirements to the Business and IT environment according to the CUI categories and types received, developed, and disseminated during the contract performance. See CMMC ePU CUI/FCI Sensitive Date Governance Policy. |
| Step 5. Risk & Security Assessment(s): Conduct a security control assessment, identify risks, and analyze each CUI Security Control or CMMC Practice and risk as you document the Risk Assessment (RA.L2-3.11) and Security Assessment. (CA.L2-3.12.1).
Identify and document the conformities (met), non-conformities (not yet met), and gaps (not yet implemented) based on the description in the implementation guidance for each CUI security control (NIST) or CMMC Practice, and each assessment objectives. Identify if sufficient evidence is available for conforming practices is available to meet the evidentiary standard. Compare your current environment to the CUI security requirements. Identify and document the conformities (satisfied/met), non-conformities (not yet satisfied/met), and gaps (not yet implemented) based on the description in the implementation guidance for each CUI security control (NIST) or CMMC Practice, and each assessment objectives. Identify the evidence to justify your assessment. All conformities (satisfied/met) require sufficient evidence. Ensure you understand the evidentiary standard. Ensure the other requirements described in the Risk Assessment (RA.L2-3.11) and Security Assessment are completed or documented in Step 6. (CA.L2-3.12.1). See CMMC ePU guidance on evidence |
| Step 6. POA&M: Identify and document ”how” the CUI security control (NIST) or CMMC Practice will address each assessment objective in the Plan of Action and Milestones (CA.L1-3.12.2).
Build the plan, schedule, and assign tasks for each item. Manage and track your progress by priority. Continuously assess your plan, activities, and tasks integrate and align with your conformities identified in Step 5. There are very important interdependencies that change in other areas easily breaks “what has already been done”.CMMC ePU implementation guidance already explains in detail “the how” and the anticipated priority required by DoD with the pending POA&M update guidance. You must tailor the CMMC ePU implementation guidance to your specific reference architecture and environment. Use the checklists provided. Identify/document the specific mechanisms, activities, and people identified within the implementation guidance “who does what” in the recommended procedures. Understand the detailed specifications and requirements for procedures. This information will be used to complete the System Security Plan (SSP). |
| Step. 7. System Security Plan: Identify all conforming (currently implemented) and not yet implemented CUI security controls or CMMC Practices, all attachments, and other items in your POA&M. A SSP is required in order to conduct the DoD Assessment for the SPRS score, though all the items may not yet be completed. (CA.L1-3.12.4)
A SSP is required in order to conduct the DoD Assessment for the SPRS score, though all the items may not yet be completed. (CA.L1-3.12.4) CMMC ePU process integrates the SSP information and attachments after they are tailored. Update the SSP with progress as you update your SPRS score in Step 8. See CA.L2-3.12.4 |
| Step. 8. SPRS: Review the guidance in the current DoD Assessment Methodology, Version 1.2. Evaluate your POA&M and the status of SUFFICIENT EVIDENCE to substanciate the score for each control.
There are no mulligans, no short cuts, and no “gimmes”. Expect DCMA to enforce the score like the IRS. Without sufficient evidence, no score is awarded. Report the SPRS score earned during steps 1-7. Update the score as frequently as desired with progress. (DFARS 252.204-7020) |
| Step. 9. Implementation: Identify, implement, and apply the CUI security controls from NIST SP 800-171r2 and other Specified CUI requirements as required by DFARS 252.204-7012.
Include all other requirements in the DFARS clause (Read the clause). Some items are not listed in NIST SP 800-171r2 or the CMMC Assessment Guide 2.0. Apply any differing guidance to the CMMC Practices or other guidance from the CMMC Assessment Process (CAP) (Read the CAP) for the purposes of certification to satisfy (and meet) all applicable CUI security requirements. These requirements are already imbedded in the implementation guidance, however you need to know the specific requirements which are NOT included in either NIST or CMMC references. See Sensitive Data Governance Policy on CUI. |
| Step 10. Implementation: Ensure each CUI security control/CMMC Practice is implemented as intended, and the implementation is consistent with CMMC ePU implementation guidance, document any modifications or tailoring needed.
Identify, implement, and document the appropriate management controls, operational controls, and technical controls to address each assessment objective. Ensure policies provide governance over all the CUI security controls/CMMC Practices within the scope of applicability (NIST) and within the CMMC scoping guidance. (NIST SP 800-171r2 and CMMC Glossary)Follow the guidance from each CMMC ePU Recommended Procedures Tables to develop specific procedures to support the implementation, operation, monitoring, and enforcement of each CUI security control (NIST) or CMMC Practice with all assessment objectives. Ensure each procedure describes in detail the mechanisms, activities, and identify the individuals or groups responsible. See procedures. See Step 6. See CMMC ePU discussion on evidence.Ensure policies provide governance over all the CUI security requirements or CMMC Practices within the scope of applicability (NIST) and within the CMMC scoping guidance. (NIST SP 800-171r2 and CMMC Glossary) Follow the guidance from the Recommended Procedures Tables to develop specific procedures to support the implementation, operation, monitoring, and enforcement of each CUI security control (NIST) or CMMC Practice with all assessment objectives. Ensure each procedure describes in detail the mechanisms, activities, and identify the individuals or groups responsible. See procedures. See evidence. |
| Step 11. Operation: Ensure each CUI security control or CMMC Practice is operating as intended by addressing each assessment objective. Controls/Practices must be monitored and enforced using a combination of management, operational, and technical controls (mechanisms, activities, and people). Meet all the requirements related to the entire CUI Lifecycle. Ensure sufficient evidence is documented. Maintain the evidence for the purposes of demonstrating eligibility, supporting audits (NIST SP 800-171A, SPRS, DIBCAC Medium/High), and certifying after an assessment (CMMC). See CMMC ePU Implementation Guidance Table 2, Step 6/10, Procedures. See CMMC ePU discussion on evidence. |
| Step 12. Operation: Ensure each CUI security control/ CMMC practice is producing the desired outcome which is necessary to satisfy all of the applicable Basic/Specified CUI security requirement(s) identified in Table 3. according to the categories of CUI received, developed, or disseminated (shared). Meet all the requirements related to the CUI Safeguarding Lifecycle. Ensure sufficient evidence is documented. Maintain the evidence for the purposes of demonstrating eligibility, supporting audits, (NIST SP 800-171A, SPRS, DIBCAC Medium/High), and certifying after an assessment (CMMC).
Document the evidence which demonstrates the outcomes are monitored, enforced, and check/audited/updated on a consistent and reasonable schedule. (NIST SP 800-171A, SPRS, DIBCAC Medium/High, and certifying after an assessment (CMMC). See CMMC ePU checklists, recommend procedures, and assigned tasks. Remember- each procedure should include the details of the management, operational, and technical methods (mechanisms, activities, and responsible parties) for verifying and validating the expected outcomes address each assessment objective as they described within the System Security Plan. Check the SSP to ensure it matches/aligns to your actual procedures. See Step 6/10, Procedures. See CMMC ePU discussion on evidence. |

Recent Comments