Since December 31, 2017 the Department of Defense (DoD) cybersecurity compliance requirements have begun to shift the landscape under U.S Defense industry contractors, suppliers, and sub-contractors. These companies are required by US Code of Federal Regulations (CFR), statutory regulations, US Government policy, and contractually obligated to meet the compliance requirements regarding Controlled Unclassified Information (CUI) created, received, stored, and shared on non-federal, covered contractor information systems as mandated by the Federal Acquisition Regulation (FAR), FAR 52.204-21, Defense Federal Acquisition Regulation Supplement (DFARS) Clause 204.7304, DFARS Clause 252.204-7008, DFARS Clause 252.204.7009, National Institute of Standards and Technology (NIST) special publication, 800-171r1.
It’s all about the data, Controlled Unclassified Information (CUI). In a follow-on post, we will discuss exactly the definitions and categories of CUI, but the simple answer is that CUI is information that the US Government restricts to only “authorized holders” and expects your company and your employees to safeguard CUI from compromise or inadvertent disclosure.
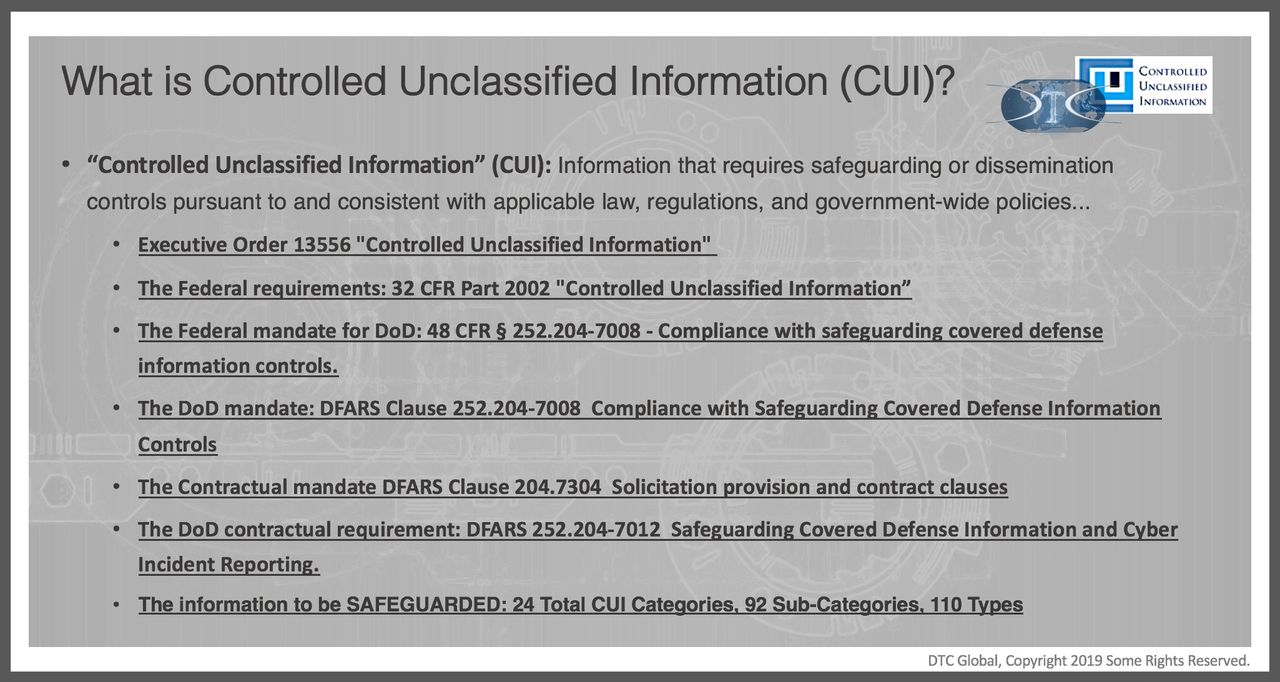
There are many categories, sub-categories, and types of CUI and CUI takes many forms… again for simplicity, for the Defense Industrial Base should generally think of CUI as technical information or the representation of technical information. The golden rule for CUI is the controls and restrictions follow the data… everywhere the data moves within the business process and everywhere the data is displayed, stored digitally, physically, or transmitted within the work environment AND enterprise IT network and devices.
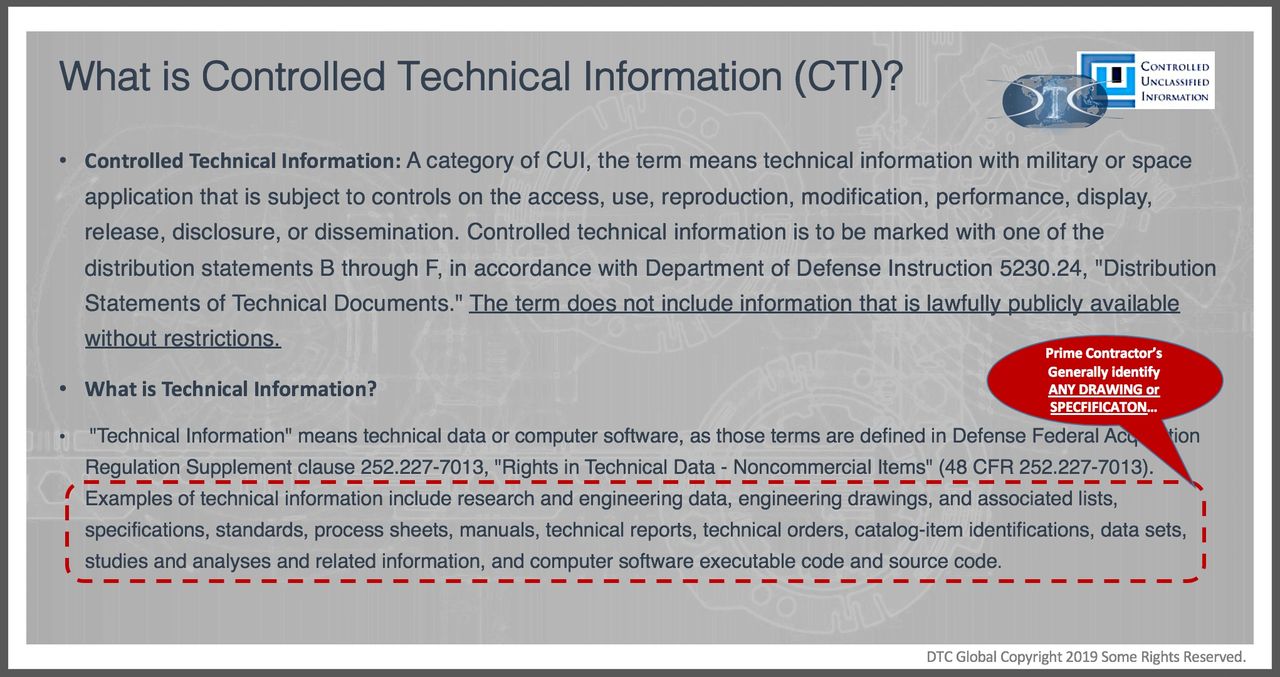
Prime Contractors generally identify ANY DRAWING or SPECIFICATION as restricted technical data (CTI). Examples of forms of restricted technical information include research and engineering data, engineering drawings, and associated lists, specifications, standards, process sheets, manuals, technical reports, technical orders, catalog-item identifications, data sets, studies and analyses and related information, and computer software executable code and source code. The physical representation of that restricted technical information as machined parts, is likely CUI. An important distinction is CUI isn’t publicly available. So if the technical information is publicly available, it’s doesn’t likely qualify as CUI.
Before you ask, of course it should be properly marked… but 90% of the CUI across DTC Global’s clients, is never properly marked. Yes, it is the government’s responsibility to properly identify and mark CUI… but the reality is that as a “new” category of marking unclassified information, both contracting officers and government program managers don’t consistently meet those obligations. Prime contractors also notoriously still use legacy markings, improperly mark documents, or in the confusion remove legacy markings, but haven’t yet fully implemented CUI marking requirements for restricted technical drawings, etc.
ITAR controlled items and documents are the exception, some companies lack understanding and expertise, and EVERY document is marked ITAR…which is helpful to identify CUI, but not helpful in many ways. Within the CUI Registry, ITAR isn’t a valid marking for CUI and specified Export Controlled Information. If all documents are marked as ITAR, and safeguards are not consistent within the business process, then employees don’t really know what is important to protect and what is not. When organizations tend to try to protect everything, more often what happens in reality is they don’t protect anything. The documents containing sensitive Export Controlled Information are often “somewhere” on the factory floor.
No markings, No problem….Wait, there’s always a catch. The Federal Code of Regulations clearly states, if information meets the definition of Controlled Unclassified Information or a category of CUI such as Export Controlled Information, then it is CUI regardless of whether it is properly marked or not, and the authorized holder (that’s YOU) is responsible for properly marking, handling, and safeguarding the CUI.
32CFR Part 2002.20 Section (a)(ii)(7) “The lack of a CUI marking on information that qualifies as CUI does not exempt the authorized holder from abiding by applicable handling requirements as described in the Order, this part, and the CUI Registry.”
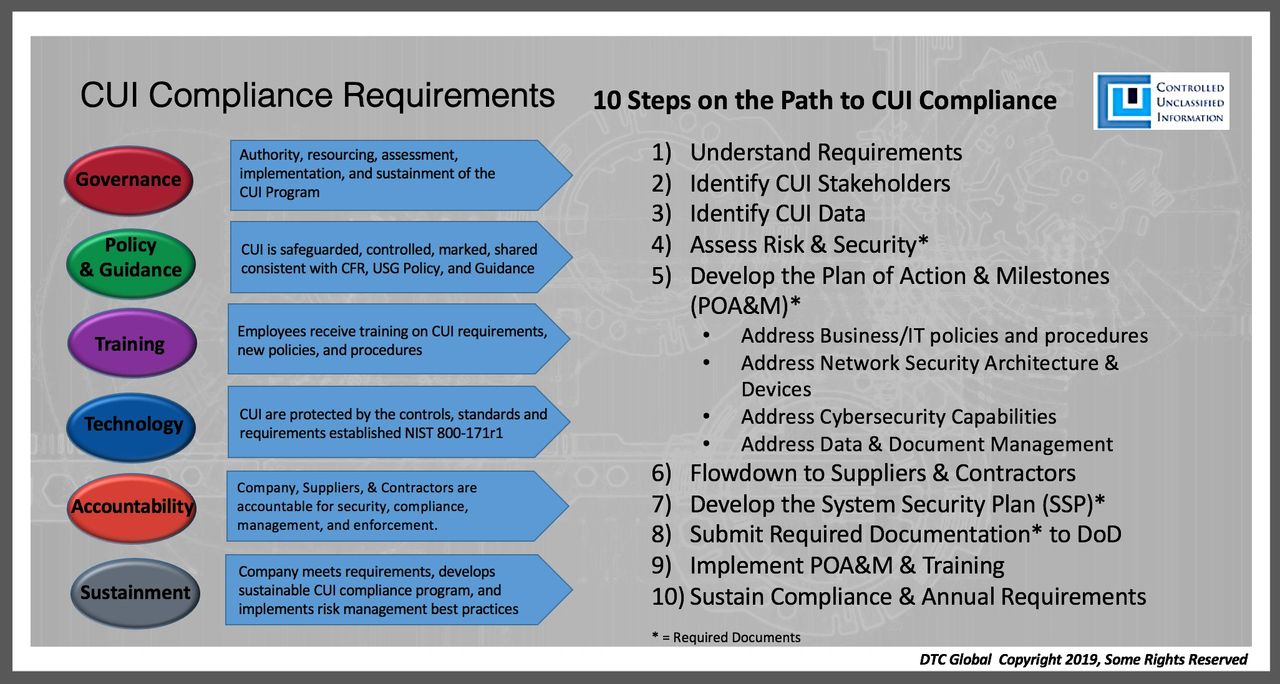
What are the 10 Steps on the Path to CUI Compliance? Every CEO always wants the cliff notes version in 30 seconds or less… CAUTION: Taking the test after reading only the cliff notes is unwise.
- Understand the Requirements
- Identify the CUI Stakeholders
- Identify the CUI Data
- Assess the Risk and Security
- Develop the Plan of Action and Milestones (POA&M)
–>Address the Business/IT Policies and Procedures
–>Address Network Security Architecture & Devices
–>Address Cybersecurity and Monitoring Capabilities
–>Address CUI Data, Document, and Records Management
- Flow down to Suppliers & Contractors
- Develop the System Security Plan (SSP)*
- Submit Required Documentation* to DoD
- Implement POA&M & Conduct Training
- Sustain Compliance & Annual Requirements (Enforce, Archive Records, Audit)
The gap between IT controls and business processes is treacherous. NIST 800-171 details the controls and requirements for company IT networks and devices containing CUI, what often gets overlooked is the impact of those controls on the business, business processes, and work instructions employees follow in their daily activities. Information is the most precious commodity a company manages, so the impact of new policies, procedures, and requirements has a substantial impact on employees who handle CUI on a daily basis. Writing stuff down is time consuming and many company’s follow mostly unwritten procedures for their day to day activities with a few written procedures for others. Implementing NIST controls effectively requires a bridge between the IT and business functions.
Free or Bulk Purchased Policy Templates? Beware of using free or commercially available templates. More often than not, the majority of IT policies lack sufficient detail and their writers lack a sufficient understanding of the NIST requirements to write an effective policy that meets requirements and helps you implement, sustain, and enforce NIST controls. In our client’s experience expensive “NIST Compliant” policies are written as stand alone documents and a significant amount of work is required to “make sure” they actually address all the NIST controls, and then integrate them into your existing policies or the other policies needed. Do your Access Control, Configuration Management, Mobile Devices, and Remote Access Policy need to seamlessly integrate? Yes, and working through lunch or between help desk tickets is only going to created inconsistencies and gaps in your policies. It’s a bad idea. Ultimately, governing IT policies are only as useful and effective as the knowledge of the author(s) on the NIST controls and their knowledge regarding how all the NIST control families would together the create a more secure environment. Implementation/Review/Audit checklists for each policy make this ESPECIALLY user friendly.
Hope is not a method. Most companies struggle with meeting requirements for various reasons. Many of our client’s approach us frustrated after spending considerable internal time and resources and still not yet compliant. Some companies have been waiting quietly with a “look and see” attitude regarding enforcement. Many companies believe they are compliant (to some degree), when in fact, they are not. The further down the supply chain to Tier 3 and Tier 4, the more vague the understanding, and the more well-intentioned business leaders struggle to understand the requirements, understand their current state of non-compliance, and the growing risk that’s being created with the passage of time.
Many companies have tried to implement the requirements, but the tyranny of the urgent prevails in preempting and preventing the internal focus and collaboration needed between critical business stakeholders and the IT support team tasked to bring their company to meet NIST 800-171 requirements. No one looks forward to heavily revising or creating IT policies that articulate the complex security standards, integrating NIST controls, reviewing the IT architecture, and aligning the daily work activities of employees that handle Controlled Unclassified Information. Then revise all the work instructions to reflect a sustainable reality. Don’t forget the training…. you get my point, but it has to be done, because there is a storm coming in 2020. Let’s do this TOGETHER, and begin today.
Recent Comments