Senior Partner at ComplianceForge | Founder & Contributor at Secure Controls Framework (SCF)
Chief Operating Officer at DTC Global, CMMCsmart, and CUIsupply.com
ComplianceForge and DTC Global teamed up to write an article that provides practitioner-level guidance on Cybersecurity Maturity Model Certification (CMMC) that is focused on the practical steps it takes to get compliant with these requirements and successfully prepare for a CMMC assessment. We get these questions on a daily basis, so we decided it would be worthwhile to summarize the steps. The end result is a list of 14 practical steps to prepare for a successful CMMC assessment.
Guidance For Internal CMMC Milestones & Resource Planning
Why this is worth pouring a cup of coffee and reading, since it is not just another article on CMMC:
1. These are practical steps that can be used to develop internal project milestones for your organization;
2. These are the steps we implement in consulting engagements that are based on real-world needs to address CMMC compliance; and
3. The recommendations can be used to help justify budget/resource requests.
Below are several important acronyms that you must be familiar with in terms of CMMC and these are used in this article (our apologies if that seems redundant but many people are not familiar with these acronyms that are common to NIST SP 800-171 and CMMC):
- C3PAO – Certified Third-Party Assessment Organization
- CMMC-AB – Cybersecurity Maturity Model Certification – Accreditation Body
- CUI – Controlled Unclassified Information
- DFARS – Defense Federal Acquisition Regulation Supplement
- DFD – Data Flow Diagram
- DIB – Defense Industrial Base
- DoD – Department of Defense
- FAR – Federal Acquisition Regulation
- FCA – False Claims Act
- FCI – Federal Contract Information
- NFO – Non-Federal Organization
- OSC – Organization Seeking Certification
- POA&M – Plan of Action & Milestones
- SSP – System Security Plan
- TSP – Third-Party Service Provider
Step 1: Identify The Target CMMC Level
In order to start, you have to know what target CMMC certification level your organization needs to attain. In terms of CMMC, that realistically means you are either targeting Level 1 or Level 3, since there are too many unanswered questions by the DoD and CMMC-AB on Levels 2, 4 & 5. Size and maturity considerations have no corresponding influence on CMMC levels – it is all about the data classification. CMMC is not a traditional “maturity model” and focuses entirely on the classification of data:
- If you store, transmit and/or process just FCI, then you are a Level 1 OSC
- If you store, transmit and/or process FCI and/or CUI, then you are a Level 3 OSC
CMMC focuses on business practices that are tied to data classification. For example, a landscaping company that has a DoD contract to mow lawns on a military installation could theoretically be a Level 1 OSC since the contract contains FCI. That same landscaping company will be a Level 1 OSC in 3, 5, or 10 years since its business model will keep it at a Level 1 (e.g., mowing lawns with only FCI-related contracts). There is no “continuous improvement” for most Level 1 OSCs as that example demonstrates.
There is a widely held misconception that a Level 1 OSC is going to be limited to small “mom and pop” companies, but that is an inaccurate assumption. An organization is designated a Level 1 when it only stores, transmits, and/or processes FCI, not CUI. It is possible to have a Fortune 500 organization be a Level 1 OSC with a robust, well-staffed, and mature security program. It is equally possible to have a small company with less than a handful of employees be a Level 3 OSC, even though it has no formal IT infrastructure or IT staff – just a completely virtual/remote workforce business model.
Step 2: Document FCI/CUI Data Flows
You have to know where you fit in the “data flow food chain” for regulated data (FCI/CUI) to progress any further. This is also a requirement within CMMC: AC.2.016 – Control the flow of CUI in accordance with approved authorizations.
A DFD is a method to identify the flow of regulated data (FCI/CUI). It does not have to be fancy, but it needs to accurately reflect two considerations:
- WHAT is being shared; and
- WHO is the information being shared with?
With CMMC, everything starts with the DoD from a data flow perspective:
- If you are a prime contractor, you deal directly with the DoD.
- If you are a subcontractor, you deal directly with a prime contractor.
Taking it a step further:
- If you are a prime contractor, you likely have subcontractors and TSPs that you share regulated data (FCI/CUI) with.
- If you are a subcontractor, you likely have TSPs that you share regulated data (FCI/CUI) with.
What you need to do is create a DFD that documents the data flows of regulated data (FCI/CUI):
- From a prime contractor’s perspective, the DFD should document the flow of regulated data (FCI/CUI) from the DoD to the prime contractor, to subcontractors and any TSPs that may have access to it.
- From a subcontractor’s perspective, the DFD should document the flow of regulated data (FCI/CUI) from the DoD to the prime contractor, to itself, then any sub-subcontractors and TSPs that may have access to it.
If you are not sure what a DFD is, you can Google the term for examples. The following diagram is an example DFD from Network-Diagrams.com. Please note that the DFD also serves you well when validating that your network diagram is correct in a following step, so it is important to put some effort into it to get it right.
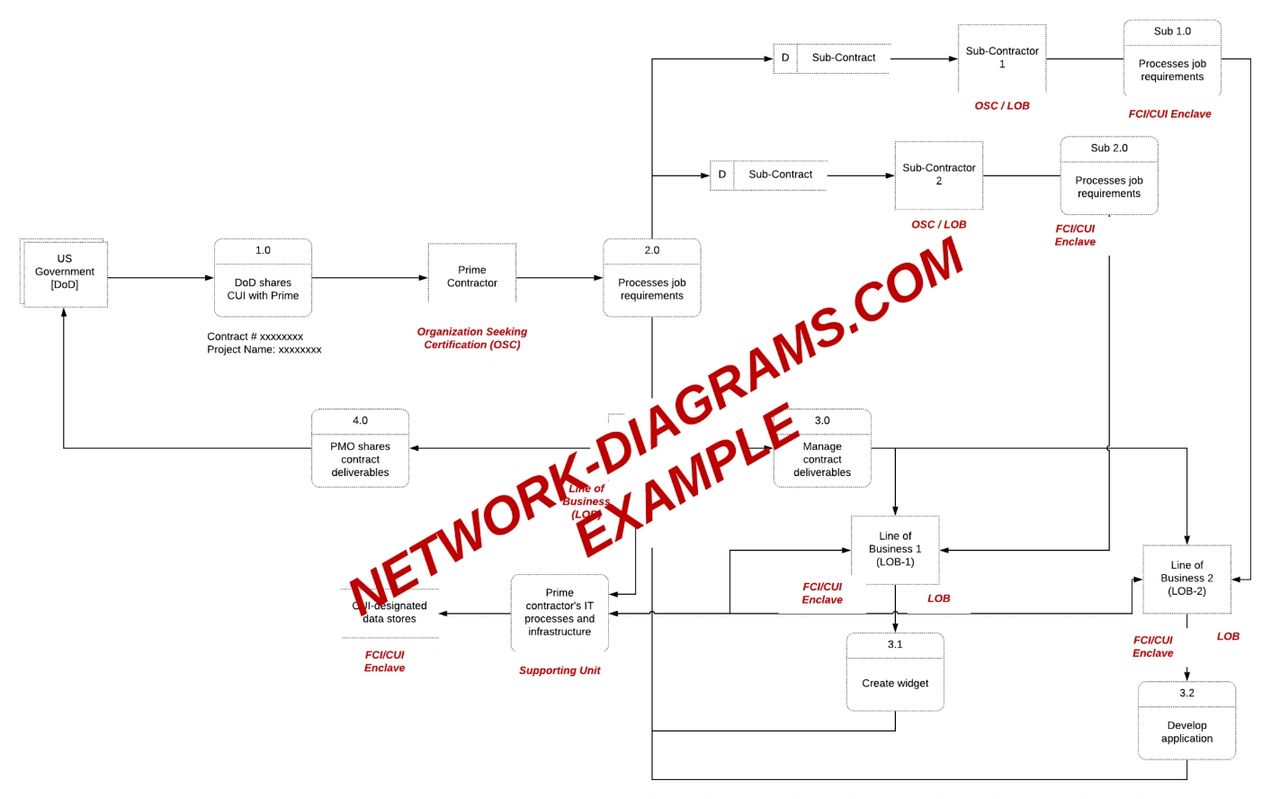
The most important part of a DFD is knowing your flow down requirement through your supply chain with CUI for level three and above. 32 CFR part 2002.16 states that the contractor must have a “reasonable expectation” to disseminate CUI to an entity that is compliant with DFARS or CMMC. As an “authorized holder” of CUI, your organization needs to reasonably expect that all intended recipients are authorized to receive the CUI and have a basic understanding of how to handle it. This means that you must be confident that any contractor or TSP you share regulated data (FCI/CUI) with is compliant and trained on how to handle CUI responsibly. From a legal perspective, you are responsible for the data you share/transmit. Documentation will be key to demonstrate evidence of that reasonable expectation (e.g., attestations, formal contracts, CMMC assessments, etc.).
Step 3: Update Asset Inventory
You have to know what assets you have to progress any further. Asset inventories are reasonable expectations in numerous laws, regulations, and industry practices. CMMC is no different in expecting accurate IT asset inventories: CM.2.061 – Establish and maintain baseline configurations and inventories of organizational systems (including hardware, software, firmware and documentation) throughout the respective system development life cycles.
CMMC is focused on protecting the integrity and confidentiality of the data on the systems, applications, and services that store, transmit, and/or process regulated data (FCI/CUI). Therefore, this step requires documenting an inventory of all systems, applications, and services that includes, but is not limited to:
- Servers
- Workstations
- Network devices (e.g., firewalls, switches, NIDS/NIPS, VPN concentrators, WAPs, etc.)
- Databases
- Mobile devices
- Third-party service providers (e.g., email, file sharing, IT support, etc.)
- Cloud infrastructure instances
- Major applications (including what servers and databases they depend on)
Step 4: Update Network Diagram
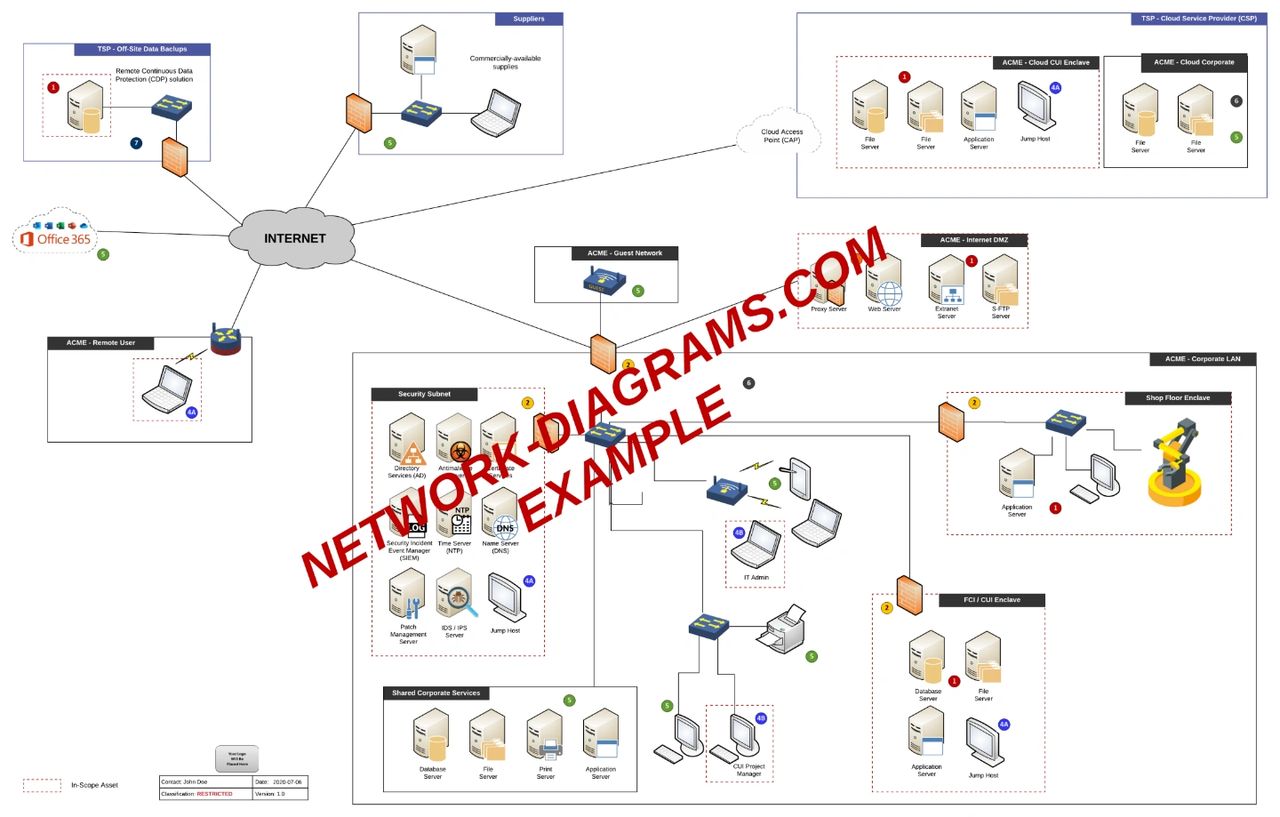
Now that you have an updated DFD and inventory, you can legitimately populate a network diagram. If you are not sure what a network diagram is, you can see examples at Network-Diagrams.com for what is a reasonable level of detail. The DoD provided specific guidance on documentation requirements that includes “A detailed topology narrative and graphic shall be included that clearly depicts the Contractor’s internal unclassified information system boundaries, system interconnections, and key components.”
A network diagram doesn’t have to be fancy, but it needs to accurately reflect:
- System boundaries (e.g., logical and physical segmentation)
- Key hardware components (e.g., firewalls, servers, databases, directory services, proxies, etc.)
- TSPs (e.g., Managed Service Providers (MSPs), bookkeepers, consultants)
- Cloud Service Providers (CSPs)(e.g., AWS, Azure, Office365, etc.)
- Subcontractors.
The following diagram is an example network diagram. As mentioned earlier, the DFD should be used to validate the accuracy of the network diagram. If the DFD does not line up, you need to determine the root issue for the disconnect to either update the DFD or network diagram.
Step 5: Define CMMC Assessment Boundary
You have to know what your CMMC assessment boundary is to progress any further. The concept of the assessment boundary is where the OSC defines what is and what is not in scope, based on how regulated data (FCI/CUI) is stored, transmitted, and processed. That process cannot legitimately be done without first having:
- FCI/CUI process flows (e.g., DFD) (step 2)
- Accurate inventory of systems, applications, and services (step 3)
- Current network diagram (step 4)

This step is also where you need to evaluate, as an organization, where you can segment your environment to use the smallest possible profile to store, transmit, and/or process regulated data (FCI/CUI). The concept is simple, but the implementation is more difficult. A question in the back of your mind should be, “What is the smallest effective footprint I can have for FCI/CUI and still operate efficiently?” This will likely involve segmenting your network, which could alter business processes – that is not a bad thing since it can make business processes more efficient and secure.
The most efficient process to define an assessment boundary for NIST SP 800-171 / CMMC can be found at CMMC-Scoping.com with the downloadable NIST 800-171 & CMMC Scoping Guide for CUI & FCI: A Zone-Based Model For A Data-Centric Security Approach To Defining NIST 800-171 & CMMC Scoping document. That scoping guide not only contains a detailed methodology but also several examples that help bring the approach to life.
Step 6: Update System Security Plan (SSP)
The SSP is a “living document” that is meant to document the who/what/where/when/why/how of the FCI/CUI environment. Maintaining a current SSP is a CMMC requirement: CA.2.157 – Develop, document and periodically update System Security Plans (SSPs) that describe system boundaries, system environments of operation, how security requirements are implemented and the relationships with or connections to other systems.
Expect the SSP to be the first thing the C3PAO requests for two reasons:
1. Prior to the assessment even starting, the SSP will be necessary to scope the level of effort needed to perform the CMMC assessment; and
2. Upon starting the CMMC assessment, the assessor will need the SSP to gain an understanding of all the parts/pieces that come together to make up the FCI/CUI environment.
It is important to note that the SSP cannot have logical inconsistencies or that risks the OSC failing the CMMC assessment, since errors on such an important document can put the rest of the OSC’s documentation into question. Essentially, if you cannot get the SSP right through missing or inaccurate information, what other problems exist?
As you learn more about your network, FCI/CUI environment, third-party involvement or evolving business processes, simply update the SSP to reflect the current state of how everything is being managed. The SSP should be written that if the smartest person on FCI/CUI in your organization won the lottery and never came back to work, that someone else could pick up the SSP and completely understand both the processes involved and all the security controls that are applied to the FCI/CUI environment. If your SSP does not have that level of coverage, you should spend time upgrading it until it reaches that level of understanding.
Step 7: Update Cybersecurity Program Documentation
Concise and comprehensive documentation can be “half the battle” in an assessment. Inconsistent, incomplete or unclear documentation creates confusion that leads to opportunities for assessors to ask probing questions, which is not a good thing in a third-party assessment. Cybersecurity documentation should follow the simple rule of “Say as you do. Do as you say.”
All too often, documentation is not scoped properly, and this leads to the governance function being viewed as more of an obstacle as compared to being an asset. CMMC documentation should be concise, clearly written and have direct mapping to all compliance requirements. A multiple-page “policy” document that blends high-level security concepts (e.g., policies), configuration requirements (e.g., standards), and work assignments (e.g., procedures) is an example of poor documentation that leads to confusion and inefficiencies across technology, cybersecurity, and privacy operations. If you are not sure what you need for cybersecurity policies, standards and procedures, you can see examples at ComplianceForge.com that are specific to NIST SP 800-171 and CMMC.
For Level 1 OSCs, the documented policies, standards and procedures need to cover FAR cybersecurity requirements.
For Level 3 OSCs, the documented policies, standards and procedures need to cover:
- Level 3 practices from CMMC (contains the 110 CUI controls from NIST SP 800-171);
- Level 3 processes from CMMC (policies, standards, procedures & resource plan documentation);
- NFO controls from Appendix E of NIST SP 800-171 (you can read more about NFO controls at NFO-Contols.com)
Regardless if you are a Level 1 or 3 OSC, you need to have written policies, standards and procedures:
Level 1: Contrary to what the DoD put out in the current CMMC model (v1.02), there is a documentation requirement for Level 1 OSCs, based on existing FAR requirements. From FAR, an organization that stores, transmits and/or processes FCI is required to “apply the following basic safeguarding requirements and procedures to protect covered contractor information systems” as it pertains to those fifteen basic cybersecurity requirements. FAR defines the term “safeguarding” to mean “measures or controls that are prescribed to protect information systems.” If you look up the term “control” in the NIST Glossary, you will see that the definition refers to documented policies, standards and procedures, so there is a tangible documentation requirement to address FAR 52.204-21.
Levels 2-3: From CMMC, there are process requirements that must be addressed that have documentation requirements:
- ML.2.999 – Establish a policy that covers each domain.
- ML.2.998 – Document the practices / procedures to implement the policy.
- ML.3.997 – Establish, maintain and resource a plan to implement the policy.*
Note: The documentation surrounding the implementation of a cybersecurity program can be evidence of ML.3.997, since the budget requests, project plans or other strategic planning proves your organization has a plan to implement the policies necessary to address CMMC.
In accordance with 32CFR 2002.20 and the CUI Marking Handbook, and the Media Protection and Physical Protection Policies, CUIsupply.com offers products to label digital and physical media such as computers, computer towers, monitors, tablets, CD’s, flash drives, external hard drives, document covers, and signs.
Step 8: Train Personnel On Secure Practices
The common weak link in most organizations is the “people factor” that covers the individuals required to operate processes. OSCs are required to train its personnel on CUI handling practices, role-specific security training, insider threat awareness, and in some cases ITAR/EAR training for export control. While the Awareness and Training (AT) domain within CMMC is only required in CMMC levels 2 through 5, it is highly recommended that level 1 organizations have some sort of cybersecurity awareness and insider threat training.
Training is expected to be both at the time of hire (prior to accessing any systems or data) and annually, thereafter. This is necessary to establish and maintain a “culture of security” within your organization that security is both taken seriously and is everyone’s responsibility.
CUI training expectations:
- Identifying CUI
- CUI handling
- Sharing restrictions
- Storage requirements
- Transmission requirements
- Marking material that contains CUI
- Disposing/destroying requirements
Security training expectations:
- Keeping network equipment secure
- Protecting credentials
- Data storage
- Emailing regulated data (FCI/CUI)
- Workstation security while present and when you are away from your desk
- Terms of use / acceptable use
- External media device handling
- Destruction of digital and non-digital media
- Awareness of malicious code which is commonly released in a phishing attack
Insider threat awareness expectations:
- Know the warning signs of a staff member who may be in danger of becoming a threat to the organization or staff
- What you can and cannot say outside the workplace (regulated data/project discussions)
- Social networking awareness
- Physical security awareness
- Travel threats and protocols
Step 9: Assign Control Ownership & Document Procedures
Now that you’ve addressed the core documentation requirements, the time-consuming process begins of putting it into practice.
Evidence of both due diligence and due care is needed to successfully pass a CMMC assessment. Documented policies and standards provide evidence of due diligence; whereas, documented and implemented procedures provide evidence of due care. Documenting step-by-step procedures is the most time-consuming activity related to cybersecurity documentation for CMMC. For the most part, you cannot easily outsource this requirement to a consultant since documenting procedures requires a subject matter expert from your organization to provide input on how a process operates, which requires internal staff to take a significant role in documenting procedures. At best, it is a joint effort to develop procedures, if you are working with a consultant on that effort.
To identify the stakeholders and assign control ownership, it is necessary to formally identify CMMC-related roles and responsibilities. Realistically, this process can be as straightforward as going through the CMMC practices and assigning each practice to one or more stakeholders. In smaller companies, this might mean a handful of people do all the work. For medium-to-large companies, there will likely be dozens of teams/individuals assigned as stakeholders. These stakeholders are “control owners” from the perspective of the CMMC assessment – those are the teams/individuals who are assigned the responsibility to implement and maintain the required practice(s) to pass CMMC.
What many people fail to realize is that CMMC documentation has many different stakeholders:
- Cybersecurity / IT department: policies & standards (organization-wide focus)
- Project team: SSP, POA&M, DFD & network diagram (contract-specific focus)
- Control owners: procedures (process-specific focus)

Step 10: Perform Quality Control & Validate Assumptions (Risk & Security Assessment)
Relying on assumptions will cause you to fail a CMMC assessment. This is where it is vitally important to conduct independent “quality control” activities to ensure that CMMC-related work is being done properly. This is where you need to validate any assumptions to identify if gaps exist and then adjust accordingly. When working with project teams and control owners, you need to operate by the “trust but verify” mindset to look at evidence of compliance and not on assumptions or undocumented practices.
There is an annual requirement for a risk and security assessment. This is an excellent opportunity for your organization to touch all systems/applications/services and determine if any deficiencies exist in their compliance program which provides the foundation for the POA&M.
Step 11: Update Plan of Action & Milestones (POA&M)
Starting in Step 8, as stakeholders start getting into the details for how CMMC practices are implemented, deficiencies will likely be identified. This is completely expected, and deficiencies must be tracked through remediation via a “risk register” or POA&M document. This provides evidence of due diligence and due care specific to the identification and remediation of CMMC-related deficiencies.
Even though the DoD is putting out conflicting guidance on POA&Ms as it pertains to CMMC assessments, having a POA&M is a CMMC requirement: CA.2.159 – Develop and implement plans of action (e.g., POA&M) designed to correct deficiencies and reduce or eliminate vulnerabilities in organizational systems.
As it currently stands, the DoD is requiring a completed or blank POA&M for an OSC to successfully pass a CMMC assessment. If there are any open deficiencies, that will cause the OSC to fail the CMMC assessment. Therefore, it is vital to perform the quality control processes called out in Step 9 to ensure there are no areas of non-compliance.
Step 12: Conduct Pre-Assessment Testing
Similar to Step 9 with an internal quality control process, it is common practice to conduct pre-assessment testing to mimic a C3PAO assessment. This is a cost-saving measure since it does not make sense to contract a C3PAO to conduct a formal CMMC assessment unless you are confident that your documentation and staff are “audit-ready” and you fully-expect to pass the assessment.
Pre-assessments should be conducted by an independent party, either internal to the OSC or a third-party (not affiliated with the C3PAO that will conduct the formal CMMC assessment). Independence is necessary to provide an honest look and remove biases, which are likely to exist when stakeholders have spent such considerable time and resources in preparation.
If deficiencies are identified in the pre-assessment testing, those issues need to be documented in the POA&M and remediated (Step 10). Ideally, the person/team who conducted the pre-assessment testing should be used to validate the remediation efforts were successful.
Step 13: Identify & Contract A C3PAO
Once you are confident that all CMMC-related practices and processes are sufficiently addressed, this is when the OSC is ready to identify a C3PAO and contract that organization to conduct the formal CMMC assessment. More details are forthcoming from the CMMC-AB and DoD on how an OSC will be able to select a C3PAO. If you are an OSC, the CMMC-AB created a page to address OSC-specific concerns about the certification process.
Once the OSC has selected a C3PAO, the C3PAO will need to conduct some form of fact-finding to scope the assessment. This is likely where an OSC will be expected to securely share information (e.g., SSP) so the C3PAO can legitimately identify the level of effort required to conduct the CMMC assessment (e.g., travel to locations, specialized technologies, complexities, etc.).
Step 14: Conduct CMMC Assessment
The CMMC-AB is working on the details that will govern the actual assessment process, so more information is forthcoming from the CMMC-AB on what to expect during the assessment, as well as how results will be reported to the DoD. Once you successfully pass the CMMC assessment, that is when your organization will be reported to the DoD as being “CMMC compliant” with a passing score (or conversely as non-compliant with a failed assessment).
Ongoing “Care & Feeding” For NIST 800-171 & CMMC Compliance
CMMC compliance does not end once an OSC passes a CMMC assessment. Underlying NIST SP 800-171 compliance is still required on an ongoing basis, where failure to maintain compliance may result in an FCA violation. While CMMC assessments are designed to be 3-year cycles, NIST SP 800-171 is a 24×7 requirement, so that is an important consideration to keep in mind that compliance does not end once an OSC successfully passes a CMMC assessment.
About The Authors
- Tom Cornelius is the Senior Partner at ComplianceForge, an industry leader in cybersecurity and privacy documentation. He is also the founder of the Secure Controls Framework (SCF), a not-for-profit initiative to help companies identify and manage their cybersecurity and privacy requirements. ComplianceForge offers extensive CMMC-focused documentation solutions.
- Les Terrell is the Co-Founder and Chief Operating Officer (COO) for DTC Global which focuses on helping businesses achieve sustainable pre-audit compliance to promote future growth and stability in the Defense Industry Base. DTC Global also operates CMMCsmart.com as paid incremental support to companies who are doing a DIY approach to CMMC, and CUIsupply.com as the only commercially available Media Protection CUI compliant supplies in the U.S.
Recent Comments