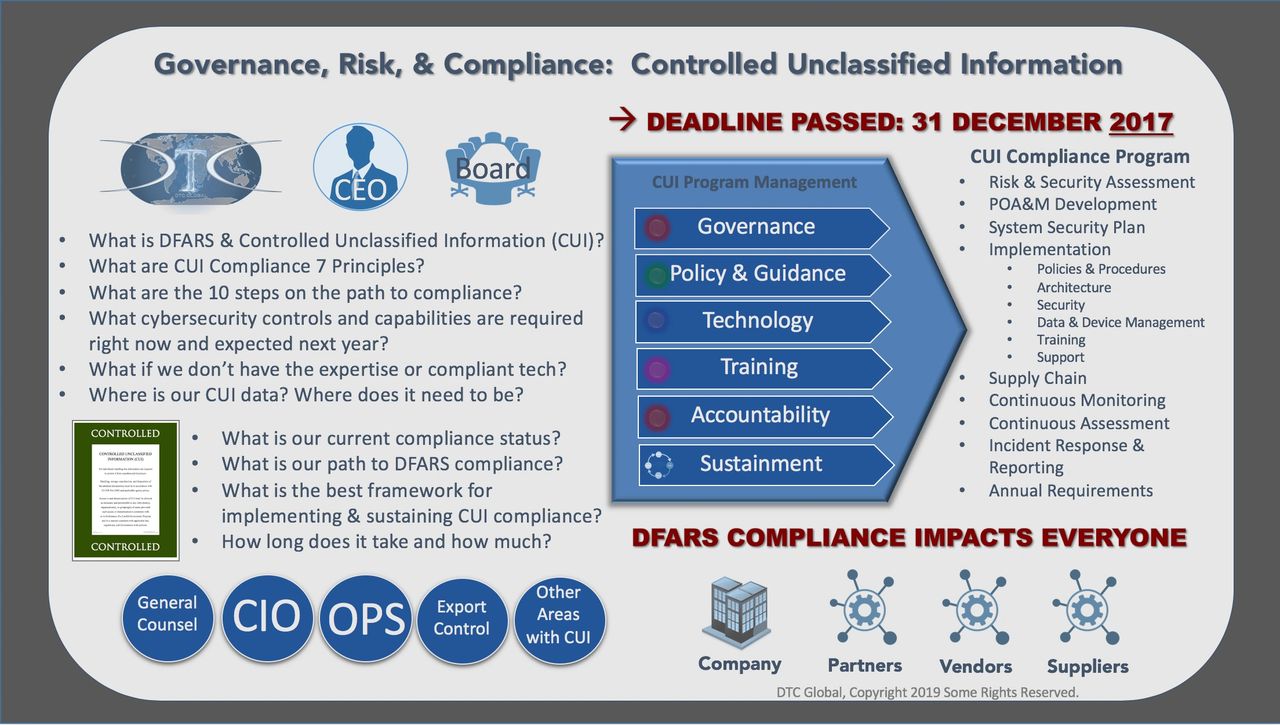
A storm is brewing for the Defense Industrial Base impacting hundreds of thousands of companies and research institutions. For the defense industry, December 31, 2017 was a critical deadline. Controlled Unclassified Information (CUI) is the compliance risk management topic every Defense Industry and research institutions’ Board of Directors, CEO, CIO, General Counsel, and COO should be discussing. Cyber security vulnerabilities and regulatory compliance requirements are two very challenging areas for most organizations. “Controlled Unclassified Information” (CUI) includes 124 categories and subcategories of unclassified information, which is required to be protected by existing Federal law, statutory regulation, and government-wide policy. Executive Order 13556, U.S. Code of Federal Regulations, Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, National Institute of Standards and Technology (NIST) Special Publication 800-171, and CUI program guidance from the Information Security and Oversight Office within the National Archives and Records Administration (NARA) give very specific new requirements for safeguarding, handling, and marking CUI data. These CUI requirements are mandated to all Federal and Non-Federal organizations if they handle, store, process, create, and transmit CUI data. CUI mandates impact the entire operations and Information Technology (IT) enterprise with the proliferation of data across emails, devices, hard drives, and printed materials. The organizational wide impact of these new CUI and cyber security compliance mandates is complicated, messy, and far bigger than an IT problem, and the DFARS deadline is long since passed with expanding requirements and more aggressive enforcement looming ahead.

These challenges can fall below urgent day-to-day tasks and other business priorities. Defense industry and research organizations often struggle with compliance requirements. Export control compliance programs provide a meaningful example of compliance risks that have a broad organizational impact. And yes, Export Controlled information (EXPT) is a specified category regulated by the new CUI requirements. (Source) Lean compliance programs require cross-functional implementation, robust risk visibility, and effective risk management. Viewing CUI compliance through more than a technology lens is critical to establishing, certifying, and sustaining compliance with the DFARS and NIST 800-171. Using an export control program compliance framework to address CUI requirements will produce better results, in less time, and be more sustainable.

Does DFARS CUI Compliance, sound familiar? It should.
A clear understanding of the downside risk and penalties of non-compliance is absolutely imperative. Failure to comply by the deadline could result in being unqualified to bid on future contracts and perhaps even jeopardize the status of current contracts. Failure to sustain compliance could result in an aggressively expanding set of negative outcomes between the prime contractor, US Department of Defense (DoD) audit and security activities, and potential implications with compliance requirements for Export Controlled information (EXPT) by US State Department. CEO’s and key leaders need to ask the right questions with a sense of urgency to lead their organizations towards the successfully meeting the CUI compliance requirements beyond December 31, 2017.
New CUI mandates require disclosure of incidents involving potential compromise of CUI data within 72 hours of detection.
CEO: What is CUI? Where is our CUI?
The new CUI compliance requirements present significant challenges across a defense industry and supplier implementation. The new CUI data requirements focus on safeguarding certain types of restricted information. In some companies, data is likely to be scattered across the corporate enterprise within laptops, desktops, servers, share drives, external drives. The U.S. Government (USG) has consolidated many different types of unclassified data required by existing laws and statutes to be protected from disclosure, into a uniform set of standards for controlled and safeguarded. CUI data includes 124 categories and various sub-categories. (Source) For large defense industry companies many types of CUI data could exist in both printed and electronic format throughout the company. Many are familiar with pre-existing control markings such as “For Official Use Only (FOUO)”, “Sensitive But Unclassified (SBU)”. However, many documents that qualify as CUI are not likely to be marked at all.
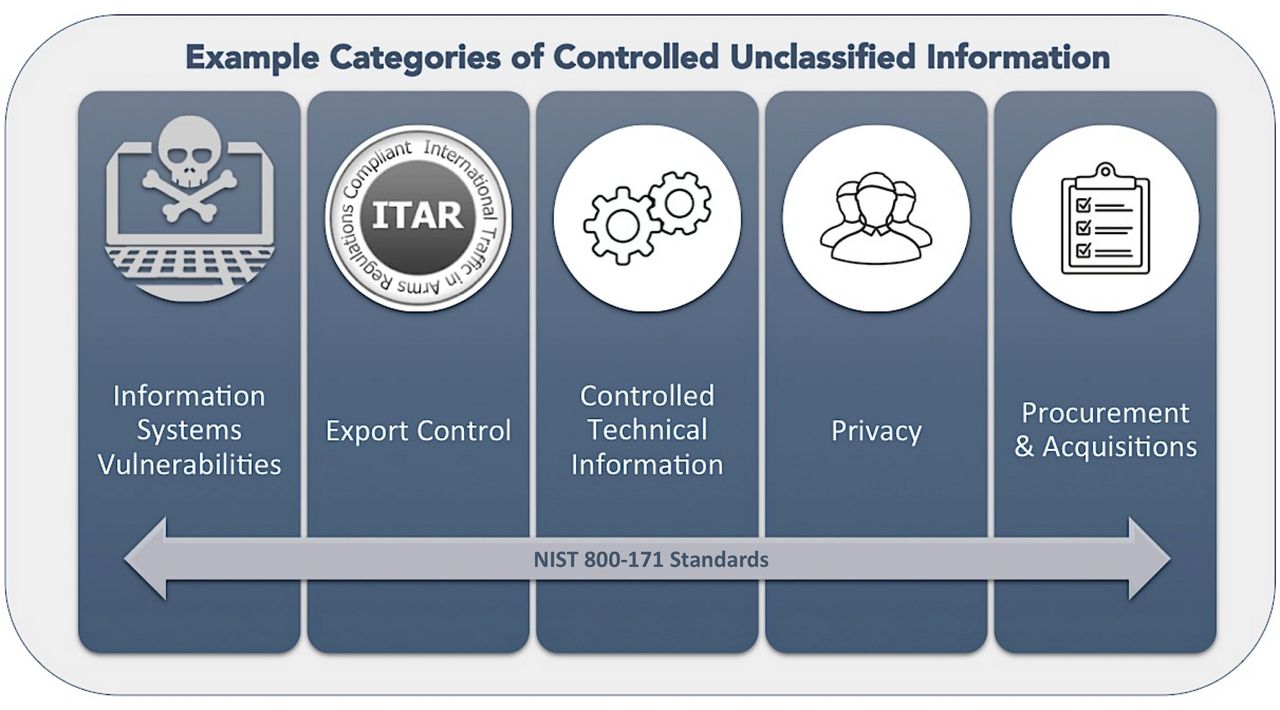
Companies may actually create different types of CUI data, including Controlled Technical Information (CTI) and Export Controlled information (EXPT). CUI data that is export controlled has specified handling and protection requirements. Export Controlled information (EXPT) is defined as, “unclassified information concerning certain items, commodities, technology, software, or other information whose export could reasonably be expected to adversely affect the United States national security and nonproliferation objectives. To include dual use items; items identified in export administration regulations, international traffic in arms regulations and the munitions list; license applications; and sensitive nuclear technology information.” (Source)
Those companies who receive, created, and handle technical information that is Export Controlled under the Arms Export Control Act (AECA), the ACEA implementing guidelines, International Traffic In-Arms Regulation (ITAR) and Export Administration Regulations (EAR). The U.S. Code of Federal Regulations, 32 CFR part 2002 requires companies meet NIST standards detailed within NIST 800-171.
A defense industry company or a supplier who produces, markets, and sells products and services through DoD contracts that are export controlled must also satisfy all DFARS requirements. This is a complex and challenging problem set because the shared ownership of CUI information among many business stakeholders across operations, research and development (R&D), engineering, manufacturing, sales and marketing, ITAR compliance, etc. to name a few. CUI data and business data are intermingled across an IT backbone blind to any differentiation between normal data and restricted CUI data categories.
Often employee access restrictions to data are limited to financial information. Employees, supervisors, and IT system administrations don’t uniquely identify, restrict, segregate, other types of “unclassified” data. Determining the types of CUI data are within the corporate-wide enterprise is critical. An organizational wide CUI risk assessment is needed and required across the entire enterprise IT network and devices to identify those devices, business processes, and projects, which involve any of the categories of unclassified data regulated within the new CUI compliance requirements. (Source)

CEO: Who are the CMMC Compliance Stakeholders?
The CMMC compliance stakeholders include all those business areas who receive, process, print, store, create, protect, and share any of the 124 categories and subcategories of CUI data. CUI compliance stakeholders include all those areas and personnel across the business functional areas who contribute to an efficient and effective CUI compliance risk management program.
The relationship among the CUI compliance stakeholders is interdependent, because the stakeholders execute tasks, use systems, and capture information, which are essential to an efficient, and effective CUI compliance program. They contribute to regulatory compliance or fuel CUI compliance risk. The participation of the CUI stakeholders is critical to establishing an effective CUI compliance program and meeting the requirements beyond the December 31, 2017 deadline.
CEO: How do we baseline our CUI risk?
Key leaders set the groundwork for establishing a CUI compliance risk management framework. The framework guides, coordinates, and unifies the parallel activities CUI stakeholders must complete across the organization in order to meet the requirements even after the December 31, 2017 deadline. The CUI stakeholders leverage the experience of internal and external resources to accelerate the assessment, development, and rollout of essential CUI compliance program components. Program components include a complex mixture of policy, procedures, and technology across a wide variety of functional areas. Consulting support during implementation will also be critical because of the constraints of time, confusion, and internal resources competing with on-going responsibilities.
Executive prioritization for sprinting towards CUI compliance is essential to accelerating the implementation, mobilizing necessary resources, and reducing organizational challenges. Although the cybersecurity controls identified in NIST 800-171 are essential to CUI compliance, focusing the effort entirely within the IT team is unlikely to result in a compliant organization. CUI Compliance risk is an operations-based, organizational wide challenge. A CUI Compliance Program is a company wide risk management initiative with critical legal ramifications. CUI compliance mandates address the cyber risks to your IT network, the day to day management of sensitive information, and the risk of inadvertent disclosure to unauthorized parties. All are high profile vulnerabilities, with significant risk, and with mandatory reporting requirements. CUI compliance represents an enduring strategic business risk with persistent vulnerabilities, and high regulatory oversight enforced with very ever aggressive consequences within the DoD and extraordinarily invasive penalties by the State Department.
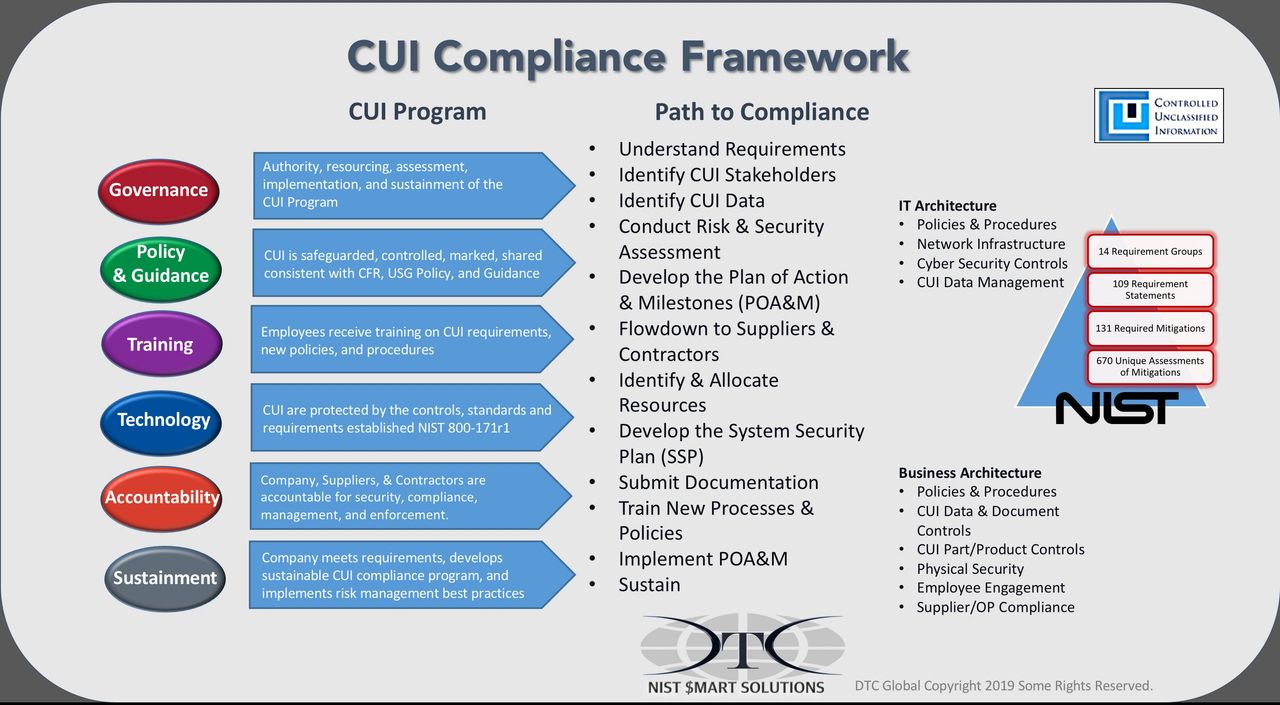
The first thing the General Counsel should do is evaluate the new CUI requirements, definitions, and assess the types of information and information systems within the corporate domain. A clear understanding of the downside risk and penalties of non-compliance is absolutely imperative. Non-compliance could result in being unqualified to bid on future contracts or perhaps even jeopardize the status of current contracts. If the evaluation of the CMMC mandates started within your organization’s IT departments, the data management and cyber security requirements focus will not likely address the greatest contributors to CUI compliance risk, day-to-day operations. Beyond the IT controls, CUI is principally an information management issue and any sustainable compliance requires a deliberate integration into on-going business operations, products, and services contract fulfillment activities. Information management, data management, and cybersecurity are PEOPLE-centric challenges, FIRST, and technology challenges, second.
Finding and properly marking data and documents required under the new compliance mandates is going to be challenging in small organizations, let alone complex organizations. CUI data likely exists across your entire network, on hard drives, emails, video, and perhaps printed in paper format. For example, CUI data that is Export Controlled (CPT) may be BOTH Covered Defense Information under the purview of DFARS 252.204-7012 AND also ITAR/EAR requirements. Technical information involved with a DoD contract or Export Controlled commodity are likely scattered across the business development, marketing, manufacturing, R&D, training, supply chain, logistics, and C-suite to name a few. A significant challenge for the Defense Industrial Base is the controls for CUI data drive requirements for specifically determining the type, location, access, marking, sharing, security, and restrictions for each category of CUI within the organization.
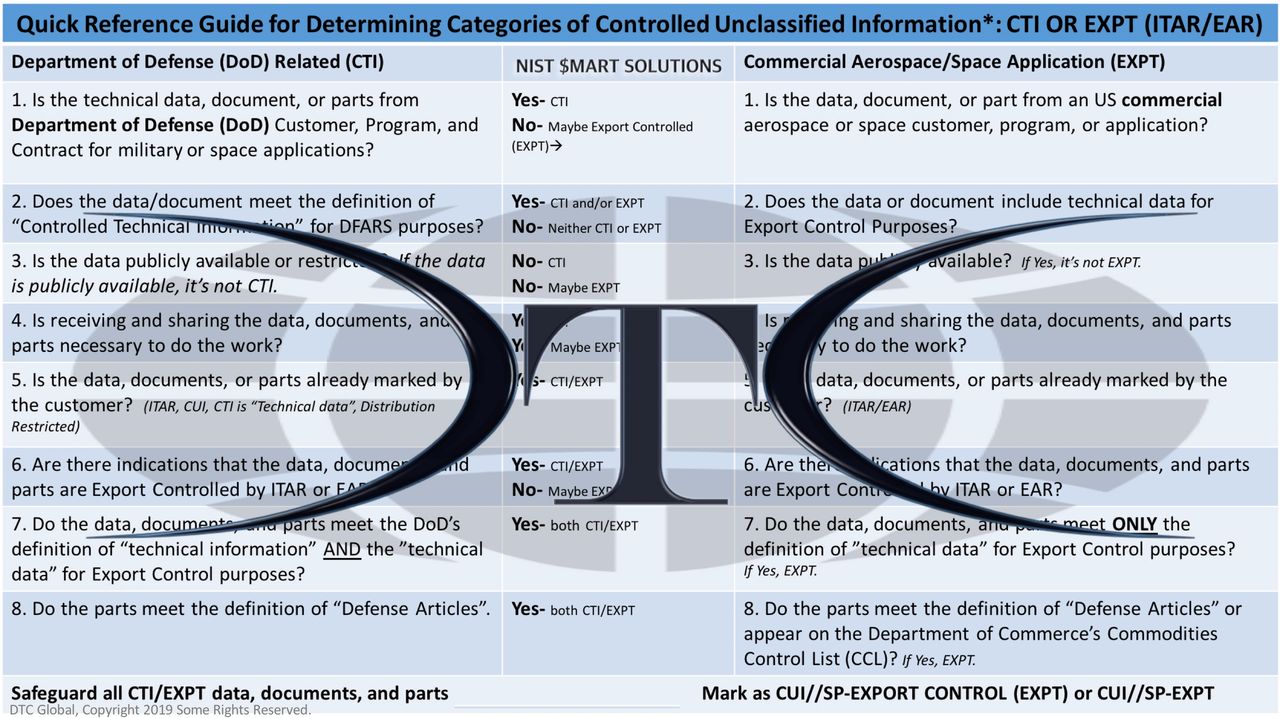
Once the CUI stakeholders work through the complex process of determining the types of CUI data they receive, create, store, and share in support of DoD contracts or those business activities which are regulated by export control regulations. The CUI data will be very difficult to find without experience to guide CUI stakeholders. CUI stakeholders must help determine “what data” is actually CUI data meets the safeguarding, dissemination, and marking requirements, and non-CUI data. During this process the data may require specialized experience, or it may be unlabeled, or perhaps even mislabeled.
A formal CUI risk assessment is required and can serve as an effective vehicle for leaders at all levels understand the risks and requirements across the organization. A CUI Risk Assessment is needed to establish the scope of CUI issues potentially lurking across the core business functional areas, physical security, as well as products and services functional areas. The CUI Risk Assessment also scopes the potential impact of the CUI mandates on day-to-day operations. The CUI Risk Assessment should identify the scope of search, types of data, and specific data features and signatures of your CUI data, so IT may use specialized tools and methods necessary to find legacy CUI data scattered across the IT enterprise.

The CUI Risk Assessment includes a network security assessment evaluating the NIST 800-171 requirements, gaps, non-conforming issues and voids to understand your risk and identify the path to compliance ahead. CUI requirements are used to evaluate current policies, procedures, and practices across business architecture (core business areas) and enterprise architecture (IT/Devices). Though NIST 800-171 Controls may seem hard to understand for non-IT employees, they include areas such as Governance, Operations, Security, Technology, Training, Risk and Compliance (GOSTT-RC) organizational areas. DTC Global’s proprietary approach translates hard to understand NIST requirements into more business friendly topics within the assessment and implementation framework for our NIST Smart Solutions DYI and turnkey packages.
An organizational wide compliance program requires an effective training program that not only trains employees on CUI awareness, but also integrates relevant policies, procedures, and practices. A baseline of knowledge about CUI compliance requirements is necessary in order to develop effective solutions and meet the program implementation and sustainment challenges. Training the general employee work force also includes evaluating, certifying, periodically inspecting, and auditing performance. Defense industry and research institutions CUI compliance programs should mirror Federal Agency requirements, except when policy standards specifically identify standards for Non-Federal institutions (Corporate/Private) organizations. In a series of requirements, the USG requires CUI program training to all agencies personnel, individuals, and private organizations with handling and safeguarding responsibilities.
A CUI program should train, evaluate, and certify employees can:
- Convey individual responsibilities related to protecting CUI.
- Describe the differences between CUI basic and CUI specified.
- Identify the categories routinely handled by personnel and special handling requirements of Specified CUI.
- Understand the impact of CUI requirements within employee policies, procedures, and work instructions.
- Understand the impact of CUI requirements on Export Controlled information and procedures.
- Describe the CUI Registry, its purpose, structure, and website address.
- Identify offices and organizations with oversight responsibilities of the CUI Compliance Program.
- Address CUI marking, handling, and data management requirements.
- Address the required physical safeguards and methods of protecting CUI.
- Address CUI destruction requirements and methods.
- Address CUI incident reporting procedures.
- Address the methods for properly sharing or disseminating CUI internally and externally.
- Address the practices for properly decontrolling CUI.
- Understand network security risks and user vulnerabilities
- Recognize Insider Threats to Network Security.
Other more specialized functional areas supporting CUI compliance require specific training and knowledge as described in NIST 800-171:
- Network security and monitoring
- Network management, auditing, and accountability
- Network access control and configuration management
- Network device and user identification and authentication
- Incident Response Plan and Reporting Procedures
- Network maintenance
- Media protection for devices, documents, removable drives
- Physical protection
- On-going network risk and security assessments
- Encryption
Measuring and monitoring risk is essential to good risk governance and the key to sustaining NIST 800-171 requirements. Assessing key metric areas for developing an effective CUI compliance dashboard is absolutely critical to measure compliance, progress within POA&M projects, and continuous improvement within the process. CUI Compliance metrics improve risk visibility, evaluate the effectiveness of network tools, and support the identification of additional resources, and also provide insights to managers and leaders in evaluating effectiveness of enforcement of security policies and CUI compliance program requirements.
Assessing and understanding third party CUI risk is also critical. The CUI requirements make it clear prime contractors are responsible for subcontractors, and vendors CUI compliance when they handle CUI information. This is also a complex challenge, because meeting internal and external CUI compliance requirements all have the same deadline, penalties, and reporting requirements. A compliance gap analysis and prioritization within the CUI risk assessment help drive the program schedule and tasks. Many companies will need external consulting support across a wide variety of areas business and enterprise areas after December 31, 2017.
CEO: Is a CUI Compliance Program needed to implement, sustain, and manage CUI compliance risk?
CUI compliance is currently an unfunded requirement, but expected changes in 2020 will allow for certain expenses. How those expenses are allocated, identified, and reimbursed is not clear. Quite literally, CUI mandates are the new cost of doing business with the Federal Government. For those Defense Industrial Base companies and their suppliers whose products, R&D, technologies, and services are included within the scope of CUI mandates, the requirements are impactful and the deadline is danger close.
Often within companies, a precious few people worry about compliance risks. Unfortunately, the extensive impact of CUI compliance within an organization is far greater than those precious few. Sanctions, fines, and prohibitions will not only impact shareholder value, but may also disrupt core revenue streams and supply chain management. Addressing CUI compliance risk is a complex leadership challenge, especially across large organizations. Many compliance professionals understand compliance risks, but few understand how to align, implement, and reduce risk across the organization.
The consequences of organizations not “owning” CUI compliance risks are far reaching. Often organizations do not “own” risk very well. Leaders require knowledge, visibility, and resources to manage their organizational risks. Good corporate governance must include CUI compliance risk within their enterprise risk management process. “Strategic risks are those risks that are most consequential to the organization’s ability to execute its strategies and achieve its business objectives. These are the risk exposures that can ultimately effect shareholder value or the viability of the organization.” (Source) A CUI Compliance Program serves to implement, manage, and provide strategic risk visibility and is a business imperative for the Defense Industrial Base and their tier suppliers. Engage and embrace the organizational and people-centric realities within establishing and sustaining compliance programs, or ignore them at your peril.
CEO: How can outsourcing support accelerate our CUI Compliance Program implementation and reduce risk?
Coherently integrated experience, services, and technologies offer a remarkable accelerant to companies seeking to rapidly address CUI compliance requirements. Once developed and implemented, a CUI Compliance Program is self-sustainable. Executives and managers need the outside assistance and perspectives of quality consulting organizations who can identify the CUI challenges organizationally, functionally, and technically.

Mapping consulting capabilities to a CUI compliance risk reduction framework whose purpose is to establish compliance within the organization, bridges missing internal capabilities and risk reduction objectives. Surging consulting capabilities to drive risk-reducing outcomes enables the roadmap and tight schedule for the Board and senior leaders committed to CUI compliance. Corporate and organizational leaders with authority and compliance consultants work together to leverage findings from the CUI risk assessment to rapidly develop a strategy, plan, tasks, and schedule. Results will always outperform legacy “passive recommendations” made by typical consultants. A hands-on approach is absolutely required.
Boards and corporate leaders need to embrace those consulting firms whose reputation is tied to results, not just beautifully bound and printed documents. Comprehensive CUI compliance risk assessments should also reveal managerial and systemic compliance vulnerabilities obscured by other approaches. Consulting success must be tied to reducing organizational-wide CUI risks: Assess, Understand, Prioritize, Enable. What are the critical elements to comprehensively reducing your CUI compliance risk?
CEO: Do we fully understand the new requirements?
The Defense Federal Acquisition Regulation Supplement (DFARS) [252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting] mandates contractors (and sub-contractors) must protect CUI to the standards outlined in the National Institute of Science and Technology (NIST) Special Publication 800-171, [Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations]. The Special Publication lists 110 controls required to protect CUI in 124 different categories. The United States Government (USG) has an interest in safeguarding the CUI data from unauthorized dissemination and also has an interest in insuring the confidentiality, integrity, and availability of a company’s IT system which safeguards CUI data. The USG mandates requirements for all Federal Agencies and beyond to individuals, and corporate organizations handling any category of CUI basic and specified data.
Much like export controlled compliance regulations, the DFARS directs contractors (and sub-contractors) disclose and report when CUI data is compromised. Since most companies rely heavily on IT systems and the preponderance of CUI data is electronic, the DFARS requires cyber incidents be disclosed within 72 hours of detection to the Department of Defense (DoD). The reporting requirements for larger organizations are complex both technically and programmatically challenging. Leaders need the authority and ability to coordinate the incident response activities quickly and fluidly across complex organizations to avoid violating these requirements.

As USG pressures tighten, prime contractors are requiring companies to demonstrate their CUI compliance in order to meet the expectations of due diligence and and due care. Companies and research institutions that ignore the CUI compliance requirements to safeguard CUI information, data, and meet network security requirements place themselves at significant risk to civil, criminal, and contract penalties. Most recently the application of the False Claims Act which incentivizes whistleblowers with up to 25% of the monetary penalties for reporting their employers. In today’s cyber security environment of ubiquitous risk, the detection of a reportable incident is inevitable. With mandatory reporting requirements, an entity should be able to produce a system compliant security plan and security assessment upon request. CUI non-compliance places current and future DoD business opportunities at significant risk.
Conclusion
New Federal regulations surrounding CUI data mandates strict adherence to controls, standards, and requirements that are detailed, complex, time/resource-consuming, and often not well understood. Foreign interests aggressively target CUI data through a variety of surreptitious means within the Defense Industrial Base. Even for the most vigilant companies, urgent business pressures distract well-intentioned leaders, managers, and employees from focusing on CUI compliance requirements impacting their entire organization, far beyond IT. Often information, data, and security management requirements are a distant priority…until it’s too late, the very reason for the aggressive path forward chosen by the Department of Defense. The CUI Compliance deadline on December 31, 2017 has long since passed, and many organizations are not compliant. Executives need to acknowledge the strategic risk to their business and the necessity to establish effective risk governance. A CUI compliance program sprint accelerates successful implementation, and effectively manages the risk of sustaining compliance across your entire organization. The path toward implementation and managing CUI compliance risk is not easy, so what do we do now? We lead.
Edited, Originally published- Linkedin on August 31, 2017

Recent Comments