[Legal- All information and images within DTC Global’s published articles and website are protected under Copyright 2020-2022 and all rights are specifically retained by DTC Global regarding use, reuse, and public display. Under no circumstances, except without EXPLICIT written permission are these rights waived for any reason. All other rights are explicitly prohibited. Requests for use should be sent to [email protected]] THIS ARTICLE DOES NOT REFLECT DOD Policy, Please see the respective websites for official policy.
DFARS 252.204-7012: In 2016, we wrote a series of articles identifying the critical cybersecurity challenges facing U.S. industry. In 2020, the US Department of Defense’s (DoD) formalization of the Cybersecurity Maturity Model Certification (CMMC) framework continues with the federal rule making process and the institutionalization of the CMMC.
CMMC has built the bridge between proverbial risk and opportunity. The DIB is faced with reconciling the real costs of the luke warm response to DFARS 7012 in the recent past, embracing the urgency CMMC certification creates, and then seeking any competitive advantage within the near future. The chasm between risk and opportunity is filled with jagged words like duty, breach of duty, causation, injury, misrepresentation, consolidation, and scarcity. It’s not just about cyber, there are other significant risk factors shaping the CMMC Framework within the defense industrial and manufacturing base. Ignore those at your peril. Just as we did from 2016-2019, now we look over the horizon to bring clarity to DIB executives’ understanding of the bumpy road ahead. The conversation about CMMC for the future winners is no longer about risk, it’s about competitive advantage.
DFARS/CMMC Adoption and Risk Management Curve
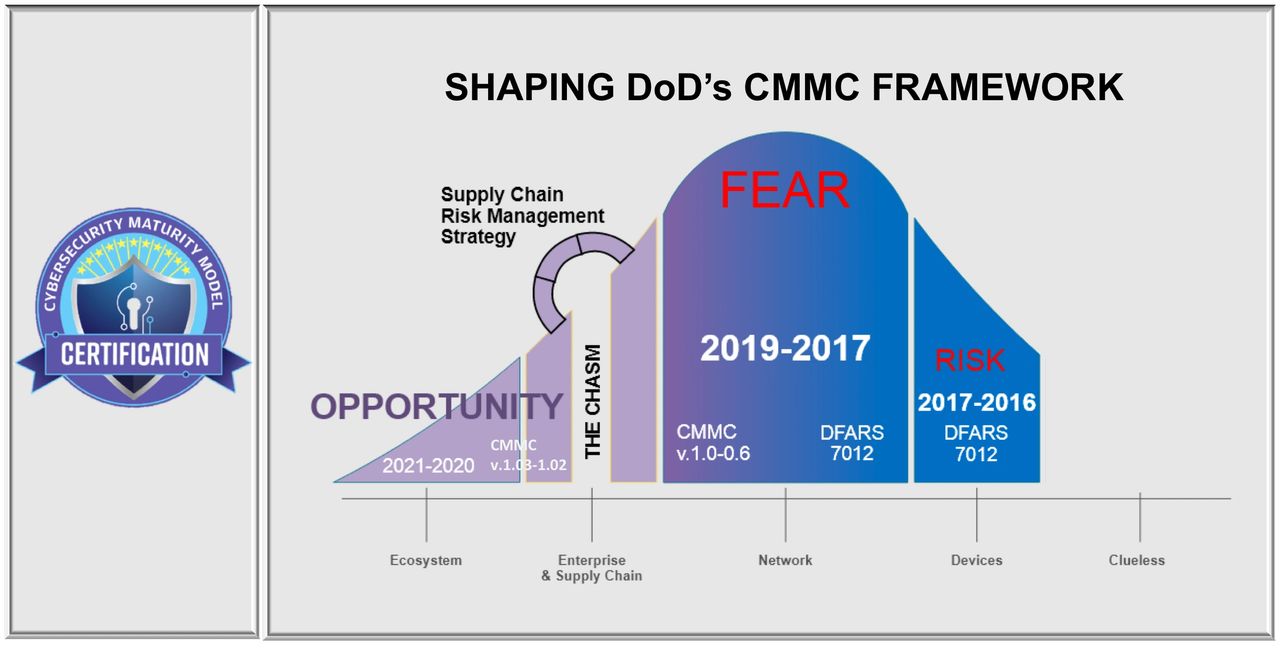
Shaping DoD’s CMMC Framework: Risk & Opportunity Factors
Five CMMC risk factors now create the chasm ahead for many, but also create significant opportunity for some. Supply chain conformity will create competitive advantage and determine future winners:
- Current high percentage of DIB noncompliance with DFARS 7012, and insufficient due diligence and due care by primes.
- Mobilization of enforcement activities; DoD’s institutionalization of cyber risk awareness; and DoD’s CMMC standards will significantly expand prime contractor’s risk and liability under DFARS 7012 and CMMC.
- CMMC readiness requires suppliers complete their Plan of Action & Milestones BEFORE they may attempt certification.
- An organization must meet 100% of the assessment requirements or 0% nonconformities for the desired CMMC Level in order to certify.
- Prime contractors that apply pressure on their supply chains without an effective Supply Chain Risk Management Strategy (SCRM) will exacerbate pre-existing industry risk factors and persistent barriers to compliance to fuel a spending frenzy, and burn time with little effect.
The next 18 months will be expensive and frustrating for most. Unmitigated, the outcomes will be low rates of supplier certification, higher than necessary (direct/indirect) costs, supply chain consolidation, and scarcity. A high stakes competitive advantage is emerging with regard to Supply Chain DFARS/CMMC conformity and risk management.

Shaping DoD’s CMMC Framework: Competitive Differentiation
For the winners, the sprint has begun towards the first major DoD program to be won and lost by their supply chain. It is only a matter of time when the DoD program managers recognize the single most effective metric to determine the risk of compromise of our next-generation warfighting capability will be to include the percentage of a prime contractor’s suppliers with CMMC certification within the evaluation criteria. There will be no other comparable metric to assess DoD’s programmatic cyber risk and non-virtual supply chain risk. In industry, few can deny the powerful impact of an effective “Quality Program” or Six Sigma implementation on a manufacturing or production environment. Quality and efficiency make all the difference. “Maturity” is the cornerstone concept for CMMC certification. Though it’s based on cybersecurity practices, certification requires a cultural transformation for most DIB organizations.
For the winners, the sprint has begun towards the first major DoD program to be won and lost by their supply chain. It is only a matter of time when DoD program managers recognize the single most effective metric to determine the risk of compromise of our next generation warfighting capability is CMMC supply chain conformity. The CMMC supply chain conformity metric is the percentage of a prime contractor’s suppliers with CMMC certification and sustains those requirements. There will be no other comparable metric to accurately assess DoD’s programatic cyber risk and non-virtual supply chain risk.
The CMMC supply chain conformity metric will be a security baseline created through shared standards. CMMC Framework enhances DIB awareness, security, and resilience through our “unity of effort” to meet and maintain those shared standards. Security is not determined by governmental fiats, compliance regimes, or the threat of punitive measures. Security is determined by people. CMMC represents a security baseline that must be institutionalized in order to be effective.
Shaping DoD’s CMMC Framework: People & Culture
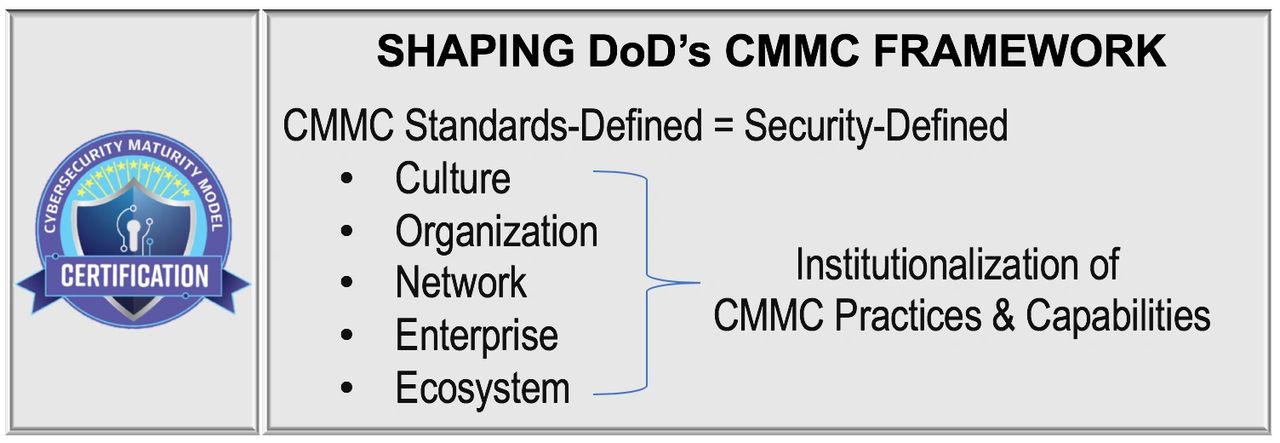
Employee and user behavior create the greatest risk and opportunity factors for every organization. Culture rules all… ideation, innovation, engineering, standardization, production, efficiency, quality, performance, and customer satisfaction…security. People are the heart of every organization. Technology is the nervous system that integrates our infrastructure to create valuable products and services. Data is our blood. A security-defined culture represents the necessity to safeguard the people, the technology, and the data from compromise. This risk and opportunity model scales from people to organizations and from organizations to ecosystems.
The purpose of the CMMC Framework is to help create a security-defined culture to safeguard people, technology, and the regulated data from compromise. The CMMC Model fulfills this purpose by influencing culture and mobilizing your people within your organization through the institutionalization of CMMC practices and requirements. Institutionalization means CMMC practices are understood and practiced by everyone…everyday.
CMMC strengthens the organizational and ecosystem phalanx through your people to build a security-defined culture.
Institutionalization means:
- Ingrained in our training & workflow.
- Ingrained in our policies & procedures.
- Ingrained in our technologies.
- Consistent. Repeatable. Meets requirements.
In industry, few can deny the powerful impact of an effective “Quality Program” or Six Sigma implementation on a manufacturing or production environment. Quality and efficiency makes all the difference. Institutionalization is the mechanism for organizational “maturity” and is a cornerstone concept for each level of CMMC certification. Though it’s based on cybersecurity practices, certification requires a cultural transformation for most DIB organizations.
Shaping the DoD’s CMMC Framework: CMMC Leadership
The CMMC Program Management Officer and the CMMC Accreditation Body fully embrace the mission to ensuring certification and any such programmatic risk decisions for safeguarding the national security interest are meaningful. CMMC certification has got to “mean something” The CMMC-AB’s Board of Directors is comprised of patriots, who are industry professionals dedicated to ensuring the independence of the AB and assessment results reflect our national security interest….in every CMMC practice. The DIB can also be confident CMMC-AB’s efforts to ensure consistency and fairness of the assessment results. The CMMC AB’s intent is to establish a robust Quality program with independent validation by DCMA’s DIBCAC program to ensure CMMC certification validates and verifies conformity with the CMMC Standard. Our collective interest is inextricably imbedded within Controlled Unclassified Information (CUI) and non-public information and communications (FCI) exchanged during the contract because they often include an organization’s intellectual property, competitive advantage, and proprietary sources and methods, The tremendous aggregate value of this data is prized by our adversaries and this harsh reality shapes DoD’s CMMC Framework. Together, we raise the bar expected to safeguard regulated data (FCI/CUI) through the certification of the CMMC Standard.
Shaping the DoD’s CMMC Framework: Supplier Challenges & Struggles
Important challenges and struggles still face many small and mid-size businesses (SMB’s), and their leaders. Implementation for most has really only just begun. A growing sense of urgency by prime contractors is displacing empathy for supply chain companies facing the significant challenges presented by DFARS/CMMC requirements. To effectively mitigate the risk factors facing suppliers, prime contractors must move beyond risk awareness seminars and develop an effective unifying strategy for their suppliers. Without it, pressure, risk, and liability will likely stress test their supply chain resilience. CMMC represents a means to create and manage a security-defined ecosystem. This effort represents a fundamental shift in both the security industry and corporate landscape, as compliance-driven digital transformation. The CMMC maturity components of the model distribute stakeholder responsibilities for data security, data management, and data compliance far beyond the CIO to leaders across the entire organization, and shared by every person.
LEVEL 6 will Shape DoD’s CMMC Framework in Five Significant Areas
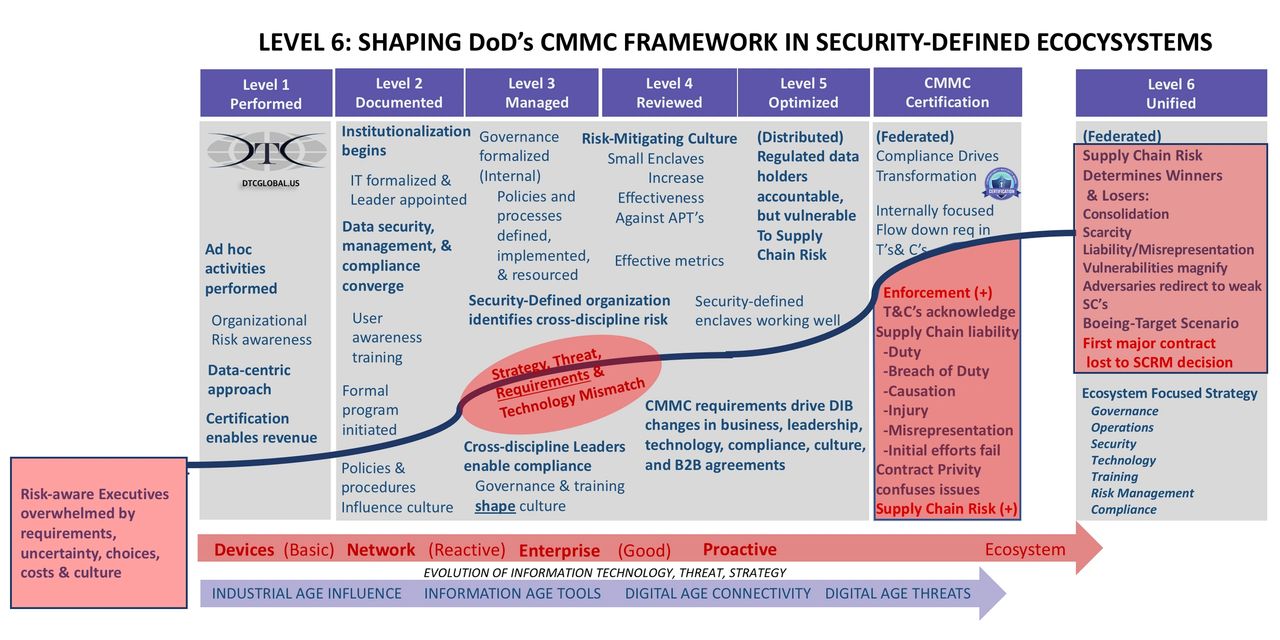
#1 The emergence of the CMMC Framework represents a convergence of business risk and the national security interest that follows the regulated data (FCI/CUI) everywhere it goes. This involves almost all core business stakeholders delivering products and services on DoD contracts. This convergence is transformational and far beyond the CIO, impacting every supplier who receives, creates, shares, transmits, and stores (FCI/CUI). For many companies, regardless of their size, or place in the supply chain, it is overwhelming.
For the DIB and CMMC, “It is governance and organizational risk management on a massive scale, spanning across private, public, industry, government, and military needs, concerns, risks, capabilities, legalities, and potentially overwhelming challenges. US cyber risk reduction requires leading without the authority to do it all…but getting it done anyway.” (Edens Dec, 2016).
#2 CMMC requires mobilization of the entire organization and Level 6 unifies the supply chain to increase supply chain conformity and reduce risk.
If the evaluation of the CMMC mandates starts within your organization’s IT departments, your data management, and cybersecurity requirements focus will not likely address the greatest contributors to CMMC compliance risk, your day-to-day operations.
Beyond the IT controls, CUI [and FCI] is principally a workflow and data management challenge. Any sustainable compliance requires deliberate integration into on-going business stakeholder activities such as operations, engineering, products, and services contract fulfillment activities. Information management, data management, and cybersecurity are PEOPLE-centric challenges, FIRST, and technology challenges, SECOND.” (Edens Aug, 2017, updated Dec, 2019)
The CMMC culture shift from a distributed to a federated model; from the emergence of a “security-defined network” to a “security-defined ecosystem; from organizational to individual responsibility for sustaining practices”. The critical relational interdependencies of culture and technology assert themselves once again. Though the last several years journey has been a confusing and difficult road for many companies CMMC requirements represent a fundamental shift within the DIB landscape and it is just the beginning. Technology is only part of an effective CMMC certification or risk management strategy:
- Prior to CMMC, admitting technology investments are expensive and insufficient, but still necessary relegated IT to a perpetual inadequate “cost center” seat at the table;
- Achieving and sustaining CMMC certification the ONLY critical path to REVENUE for those contractors and subcontractors required to be certified. Coming soon is an ugly reality: No CMMC certification is a no-bid.
- It takes FAR MORE than the CIO or IT team to mobilize and align the organization for CMMC Certification.
- Alignment of cyber governance, cybersecurity, technology acquisition strategy, operations plan, workflow accommodations, training, risk transfer strategies, AND your supply chain to reflect ground truth realities. The next step is to set the course on an achievable path to transformation…from ‘As is..To be’ in 6,12, or even 18 months. No easy task.
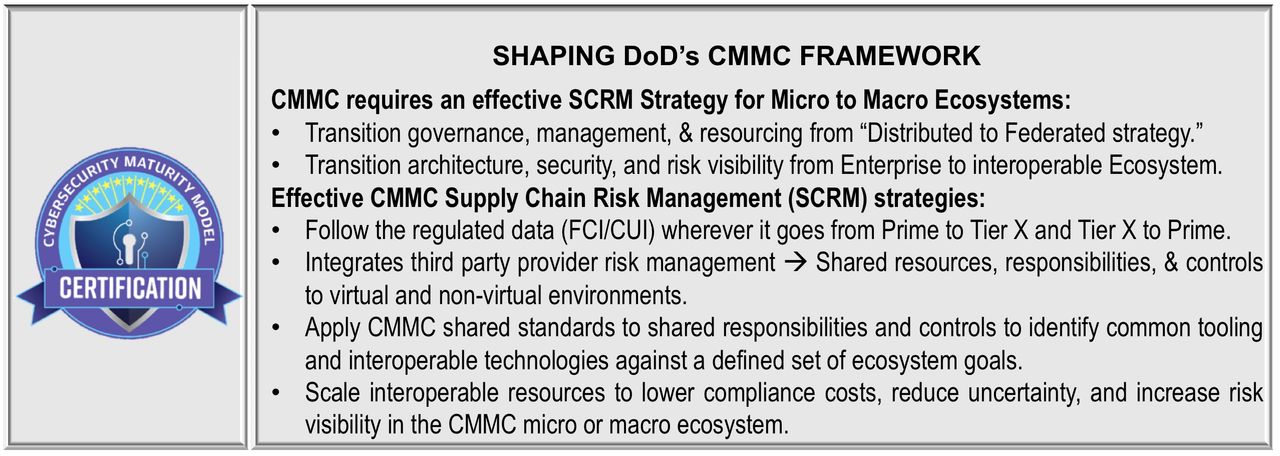
#3 Level 6 retools your CMMC Supply Chain Risk Management Strategy in alignment with CMMC requirements:
- Regulated data (CUI/FCI) holders within organizations become accountable but remain vulnerable to Supply Chain Risk, CMMC flow-down requirements, and FCI/CUI confidentiality.
- Requires a transformation in YOUR DoD contract Supply Chain Risk Management (SCRM) Strategy from demand-based acquisition to qualified supplier-based contractor availability.
- Magnifies the critical importance of regulated data (CUI/FCI) confidentiality, security, and compliance as the most important determining factors in your supplier’s DoD subcontract availability.
- Supply chain reporting integrity presents significant challenges; demonstrating risk management capabilities requires “institutionalization” within SCRM strategy, due care, and due diligence.
- Transparency for CMMC supply chain due care and due diligence expectations is needed from the Prime Contractor to Tier X.
- Suppliers Fear Transparency.
Small and mid-sized businesses are often targeted because they are more vulnerable, represent a single point of failure, or have disproportionate access to important information given their size within a supply chain. This poses a particular risk for larger companies on whom they depend.” (Edens, Apr 2016) “To deal with both the changes in business demands and the increasing sophistication of threats, security controls need to provide deeper visibility, increased accuracy of detection, and faster mitigation. Such platforms need to be driven by a security architecture that can scale across the distributed enterprise and be implemented via security processes that can work across the realities of federated environments with consistent security capabilities.” (Source)Your suppliers will likely fear transparency about their security challenges. The fear is rooted in discovering problems in which the cost of the solution [conformity] is too far out of reach. Without reliable [and shared] security standards, Your supply chain does not just lack resilience or sustainability, it is an enormous liability.Together, “we” are more vulnerable, and pretending that risk doesn’t exist isn’t an option either…the balance sheet risks for EVERYONE are just too great. All parties must embrace the significant challenges to meet CMMC requirements every company faces-lack of expertise, experience, and limited resources. For most companies, options are limited and need to be sustainable. The goal is to leverage the prime contractor’s expertise and experience in developing ecosystem-based solutions that address persistent barriers to compliance reduces uncertainty, increases transparency, and lowers/controls cost. Most importantly, the implementation of the appropriate components of an SCRM strategy enhances the chances of their suppliers for CMMC certification.
#4 An effective SCRM Strategy provides appropriate structure along with an organization’s existing maturity level and guides along a continuum in terms of the appropriate processes, practices, and capabilities required for CMMC certification and sustainment.
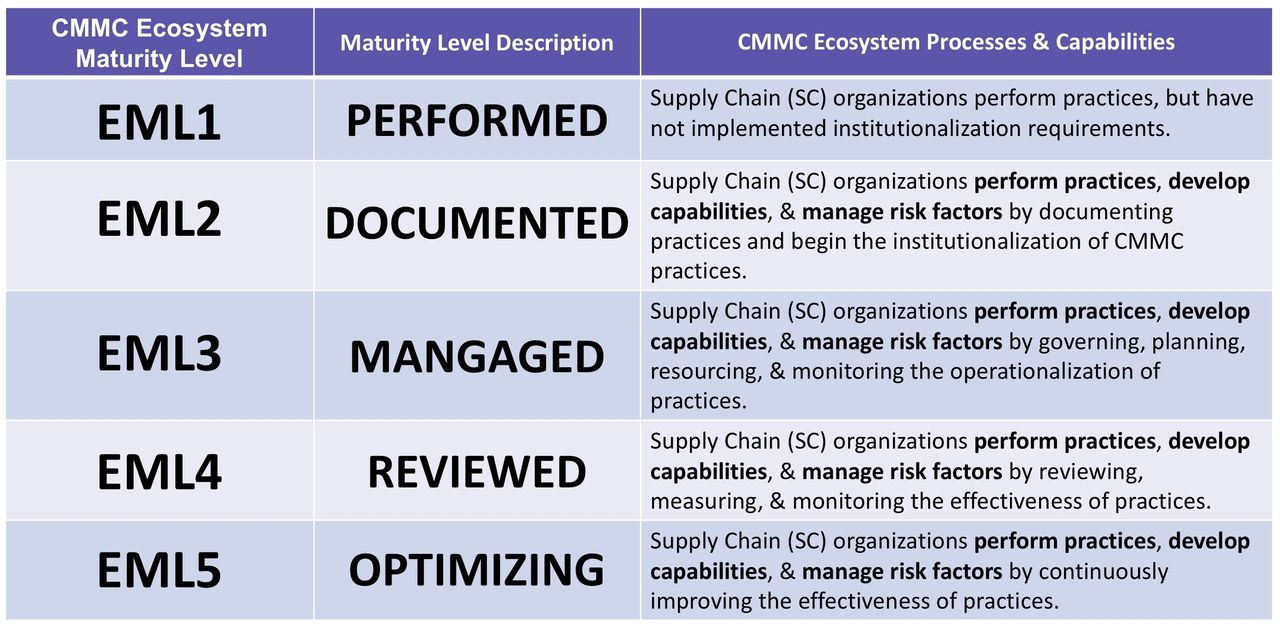
This is adaptation of the current CMMC Model, v.1,02 maturity levels to supply chain risk management to support a transition to an ecosystem approach as represented in the CMMC “Level 6” model. The model was adapted from our earlier work HERE and earlier work from Gartner.

#5 Moving Together Beyond Fear to architect and resource Security-Defined Networks, Enterprises, and Ecosystem(s). In practical terms, the differences between a Distributed IT Network Security Strategy and a Federated IT Network Security Strategy is the authority to require accountability, cooperation, and collaboration among all your third party providers, suppliers, and subcontractors who create, share, receive, transmit and store regulated data (FCI/CUI) and are essential to supporting the DoD contract. Neither the large company, nor the smaller supplier companies want intrusive access into each others’ network, but both want each of them to be protected and secure. Protecting the strength and resiliency of the supply chain necessitates the protection of proprietary interests, and keeping the data of each company secure. A cooperative IT strategy must do both. A prime contractor should understand the initial vulnerabilities, architecture, and limitations in expertise, experience, and resources of each of their respective suppliers. They share considerable risk. (Edens Apr 2016)
- YOUR Supply Chain needs reliable and hardened security that is cost-effective, scalable, and interoperable.
- YOUR Supply Chain needs to help to understand the costs, the recognition that a spending frenzy won’t “fix it” and time to resource those expenses during tough cashflow periods.
- YOUR Supply Chain needs solutions that are sustainable within their expertise, experience, and resources.
- YOUR Supply Chain needs a solution(s) that the hardening, monitoring, and reporting process protects their proprietary and competitive interests. You are important, but not likely their only customer.
- YOUR Supply Chain needs to sustain their compliance, agree to report “really” meet reporting requirements.
- YOUR Supply Chain needs to look ahead to the near-term needs to share threat intelligence, network activity metrics, and their compliance status through shared tools and resources. (Edens Apr 2016)
Shaping the DoD’s CMMC Framework: The cure can’t be worse.The systemic risk factors within defense and industrial base are real and persistent. Conducting supplier seminars on DFARS and CMMC Risk Awareness and then sending them back to islands of nonconformity without a plan and without resources to “find their own way” to meet CMMC requirements will accelerate consolidation and scarcity. The Interagency Task Force report, “Assessing and Strengthening the Manufacturing and Defense Industrial Base and Supply Chain Resiliency of the United States” is a cautionary tale that doesn’t include additional recent risk factors such as the COVID-19 impacts to the workforce, economy, and capital.

Beyond the persistent barriers to compliance facing the DIB, the cure is a jagged little pill that must be carefully managed. All the risk factors or archetypes described in detail with the report are exemplified with DFARS 7012 and CMMC. These systemic risks must be treated with systemic cures through maximum participation between prime contractors and their suppliers and your suppliers and their subcontractors. Transitioning terms and transitioning thinking along the CMMC adoption curve from Tier 1 supply chain risk to ecosystem risk management will REDEFINE competitive advantage and differentiation within the hyper-competitive defense market. Ignore this warning and these risk factors at your own peril.


Shaping the DoD’s CMMC Framework: Start picking winners NOW.Prime contractors must also begin to pick the winners now, so there is time for non-compliant suppliers to recognize the pressure is real and respond. Avoid failing to reward your suppliers who are aggressive and proactive in meeting DFARS 7012 and already preparing for CMMC. Let your best suppliers start to steal the lunch money of the DFARS and CMMC laggards, reward their relentless commitment to managing your risk and theirs.
Conclusion
Top 5 Priorities ahead… Your sense of urgency is everything. Priority #1 Star picking your winners NOW. Priority #2 Reject the notion your lagging suppliers are relegated to be nonconforming islands of misfit toys. Choose English Literature for your Jeopardy Answer: “No supplier is an island to its own.” The winners will recognize the need to proactively manage their ecosystem and the losers will see pressure, frustration, and cost force consolidation and create scarcity. Priority #3 Understand where your suppliers are (really) along the DFARS/CMMC adoption curve. Conduct a detailed supplier impact analysis of your annual spend and be realistic about business decisions ahead for YOU and YOUR suppliers. We are never going back.Priority #3 Develop a Supply Chain Risk Management Strategy that increases transparency, reduces uncertainty, and provides opportunities to leverage shared resources, tools, experience, and best practices.Priority #5 Develop a CMMC cooperative model within your SCRM strategy and ecosystem. Consider using the collective power to negotiate pricing on turnkey solutions, shared resources, and common tools. Today’s CMMC Jeopardy Question: For Whom the Bell Tolls?
[Legal- All information and images within DTC Global’s published articles and website are protected under Copyright 2020-2022 and all rights are specifically retained by DTC Global regarding use, reuse, and public display. Under no circumstances, except without EXPLICIT written permission are these rights waived for any reason. All other rights are explicitly prohibited. Requests for use should be sent to [email protected]]
Recent Comments