NOTE: All opinions are my own and do not reflect the official position of the CMMC Accreditation Body, the CMMC PMO, or the Department of Defense.
DoD Prime contractors and their suppliers, subcontractors, and tier suppliers impacted by DFARS 202.252-7012 face significant barriers to compliance. Uncertainty facing senior executives and business owners undermines the appropriate decisions, priorities, and resources necessary to address mounting enforcement pressures ahead for the Defense Industrial Base (DIB). Training is a fundamental requirement for compliance, but more importantly training is a company’s critical enabler to securing CUI and sustaining compliance.
DO NOT WAIT ON THE CYBERSECURITY MATURITY MODEL CERTIFICATION FRAMEWORK TO BEGIN, OR CONTINUE YOUR PATH TO DFARS COMPLIANCE.
On 20DEC, 2019, the National Defense Authorization Act For Fiscal Year 2020 became public law that identified certain responsibilities and authorities for the CMMC Framework Program detailed in Reference Table F at the end of the article. The CMMC program is moving forward. DoD’s efforts to secure CUI and enforce existing cybersecurity and CUI handling standards are being reinforced by the Defense Contracting Management Agency (DCMA)’s implementation of the NIST SP 800-171 Assessment Methodology. DCMA is assessing contracted DoD companies and their impacted supply chain’s current implementation of CUI requirements. Companies and their supply chains who have not yet completed their Plan of Action and Milestones (POA&M) or not actually compliant will be “outed” by the process. Expect the negative consequences to dramatically increase in 2020 across a variety of enforcement methods to drive a sense of much needed urgency and criticality within the DIB. The CMMC program will build upon the DCMA’s program as it rapidly formalizes, codifies, and launches the Accreditation Body and programmatic infrastructure over the next few months.
If your company currently handles CUI as part of your business process, the requirements for DFARS compliance have not changed and will continue to include NIST SP 800-171 standards within the CMMC certification as required by 32CFR §2002. The CMMC requirements will continue to formalize and expand over the year as the program requirements unfold. This process is all but a distraction for those companies ALREADY REQUIRED TO BE DFARS COMPLIANT. The requirements will likely be packaged differently, but the basic NIST SP 800-171 controls and those requirements detailed within 32CFR §2002 will not likely diminish, but are likely to expand under CMMC.
The path to DFARS compliance begins with learning and understanding the basic responsibilities required for handling CUI. As newly appointed CUI Compliance Program Managers, Quality Managers, or business owners try to understand these CUI requirements, they will begin to understand the actual impact of CUI requirements across their company. CUI requirements impact the businesses far beyond the normal scope of responsibilities of IT. Keeping CUI secure and addressing the genuine national security threat facing our country rests in the hands of everyone who handles CUI data, documents, and controlled items.
No matter how compelling tech companies marketing literature may be, minimizing the role of employee training and an over reliance on technology to mitigate CUI compliance risk is the equivalent to standing on the bridge of the Titanic with a warm cup of joe and a temporary smile. Sail your ship of excellence to a safe port by using employee training to safely navigate CUI compliance waters filled with icebergs. Captain your ship by charting the smart course to a clear understanding of CUI handling responsibilities and then shape your corporate culture by training your employees, monitoring behavior, and then rewarding excellence. The time to begin is NOW.

Warning: Dangerous Waters Ahead.
The significance of CUI compliance requirements ahead for all contractors doing business with the US Government, cannot be understated. DFARS current self-attestation is being verified by DCMA’s Assessment Methodology and then verified by third party certification within the new CMMC program. Moving into the third year of self-attestation since the 2017 deadline for CUI compliance, the risk is rapidly growing into legal liabilities under the False Claims Act for those companies not yet compliant. Training is the most effective compliance risk management activity an employer can do to accelerate, enable, and sustain their path to CUI compliance.
Common questions by employers struggling with understanding and meeting DFARS requirements are, “when should we train our employees? How? How often? What is the training content or which topic areas are required?” The answers require a deep understanding of NIST SP 800-171 and with 32CFR §2002. It takes a bit of CUI compliance practitioner “ninja skills” to untangle the requirements. These requirements are discussed and then important areas are broken down within Reference Tables A-E. A CUI Training Checklist is also at the end of the article. A comprehensive list of references for all things CUI related is at the bottom of the page under References and Resources HERE.
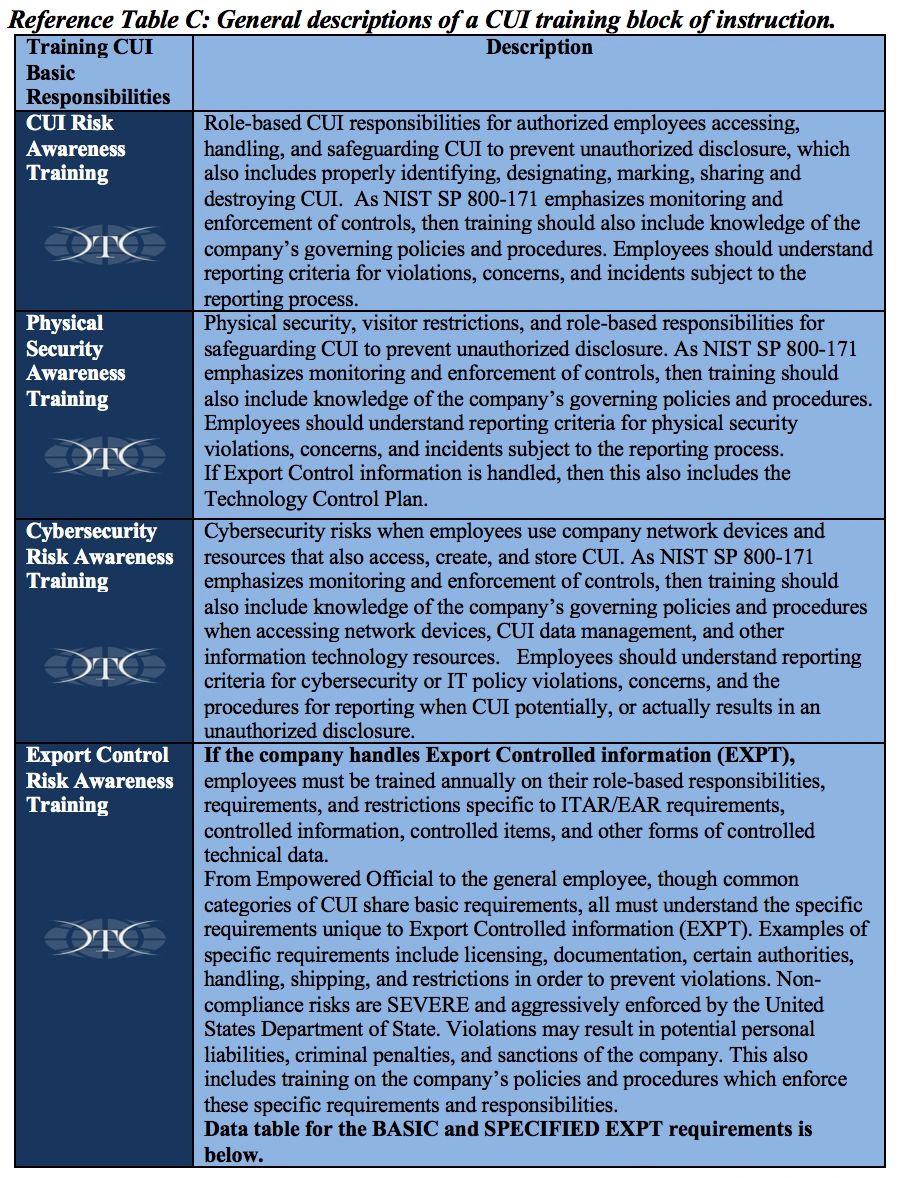
Most companies struggling with implementing DFARS compliance may be surprised to realize four major training areas are included in the “basic responsibilities and handling” provisions of 32CFR §2002 and within NIST SP 800-171.
· CUI Risk Awareness Training on role-based CUI responsibilities for authorized employees accessing, handling, and safeguarding CUI to prevent unauthorized disclosure, which also includes properly identifying, designating, marking, sharing and destroying CUI. As NIST SP 800-171 emphasizes monitoring and enforcement of controls, then training should also include knowledge of the company’s governing policies and procedures. Employees should understand reporting criteria for violations, concerns, and incidents subject to the reporting process.
· Physical Security Awareness Training on physical security of facilities, visitor restrictions, and role-based responsibilities for safeguarding CUI to prevent unauthorized disclosure. As NIST SP 800-171 emphasizes monitoring and enforcement of controls, then training should also include knowledge of the company’s governing policies and procedures. Employees should understand reporting criteria for physical security violations, concerns, and incidents subject to the reporting process.
· Cybersecurity Risk Awareness Training on cybersecurity risks when employees use company network devices and resources that also access, create, and store CUI. As NIST SP 800-171 emphasizes monitoring and enforcement of controls, then training should also include knowledge of the company’s governing policies and procedures. Employees should understand reporting criteria for cybersecurity or IT policy violations, concerns, and the procedures for reporting when CUI potentially, or actually results in an unauthorized disclosure.
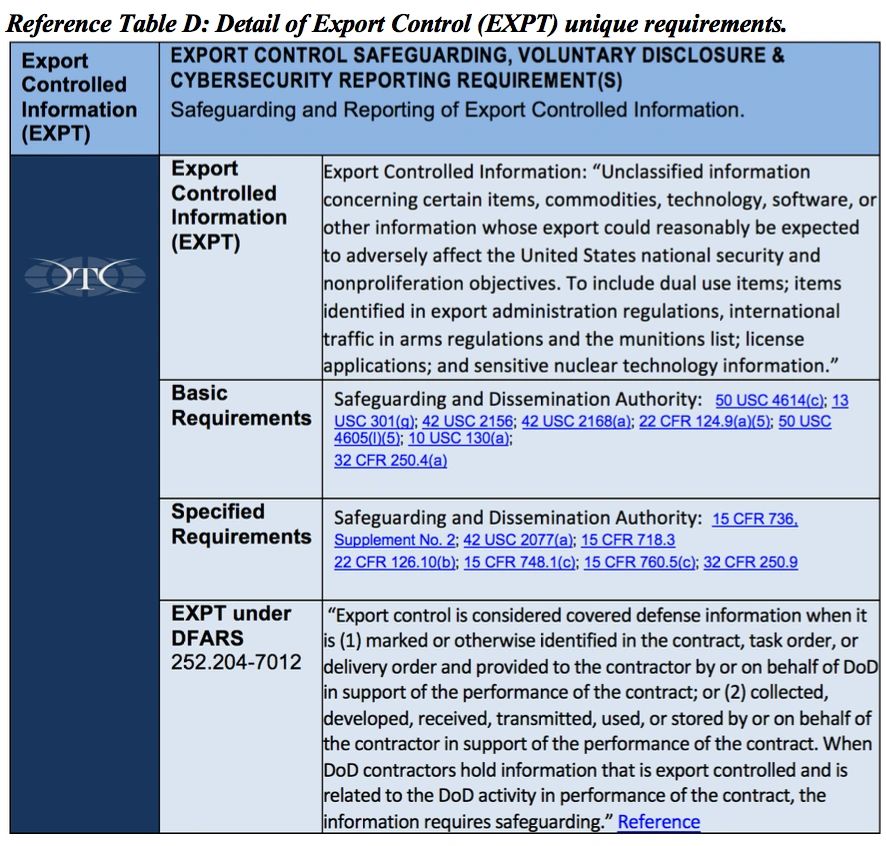
· Export Control Risk Awareness Training, if the company handles Export Controlled information (EXPT). Employees must be trained annually on their role-based responsibilities, requirements, and restrictions specific to ITAR/EAR requirements, controlled information, controlled items, and other forms of controlled technical data. See Reference Table C for additional detail.
Not for Compliance Sake.
CUI compliance is not about saving endangered red-cockaded woodpeckers (inside joke for former military readers). It’s certainly not about compliance for the sake of compliance. DFARS requirements are meant to protect Controlled Unclassified Information (CUI) from our global adversaries, who threaten our technological warfighting advantage, our national security, and our children’s future. The purpose of DFARS and NIST training requirements for CUI is to protect America’s warfighting capabilities and the lives of our Soldiers, Sailors, Airman, Guardsmen, and Marines in harm’s way. We protect them by safeguarding and proper handling CUI to minimize the risk and prevent the unauthorized disclosure of CUI.
“Unauthorized disclosure occurs when an authorized holder of CUI intentionally or unintentionally discloses CUI without a lawful Government purpose, in violation of restrictions imposed by safeguarding or dissemination controls, or contrary to limited dissemination controls.”
The Department of Defense (DoD) and most Americans recognize the extraordinary risk to our future national security, should this information continue to remain vulnerable to compromise by our adversaries and our indifference. Effective implementation and sustainment of DFARS and NIST controls requires training our employees, not just in an effort to meet the minimum requirements, but with the same sense of vigilance we would expect in protecting our children and grandchildren.
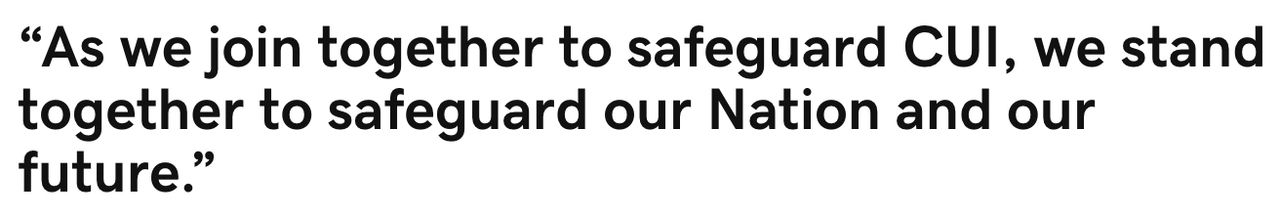
To understand CUI training requirements, we also have to understand the expectations and specific responsibilities identified with 32CFR §2002 and by the National Archives, Information Security Oversight Office. If you just asked yourself, 32 what? and ISOO who?… the risk and significance of “checking the DFARS compliance box” on your contracts and prime contractor’s self-attestations and supplier surveys continues to grow. The risk and ramifications are increasing if your company continues to conduct DoD-related business and not actually be compliant, whether with a wink, in ignorance, or far worse, willful negligence.
You can train your employees to efficiently and effectively protect CUI, protect your company, protect your customers, and deliver profitable products and services. Companies receiving, creating, disseminating, and archiving CUI must understand their basic responsibilities, understand risk areas, and communicate handling guidance to your employees. The training guidance needs to be in the context of your company’s business model, processes, and business technologies. Companies must establish governing policies and procedures. Employees must practice their CUI basic responsibilities during their day-to-day activities. Employees need to be qualified, authorized, and trained prior to receiving CUI. The controls required for CUI require consistent enforcement to be effective. Your employees need proper training and reinforcement.
Understanding CUI Requirements.
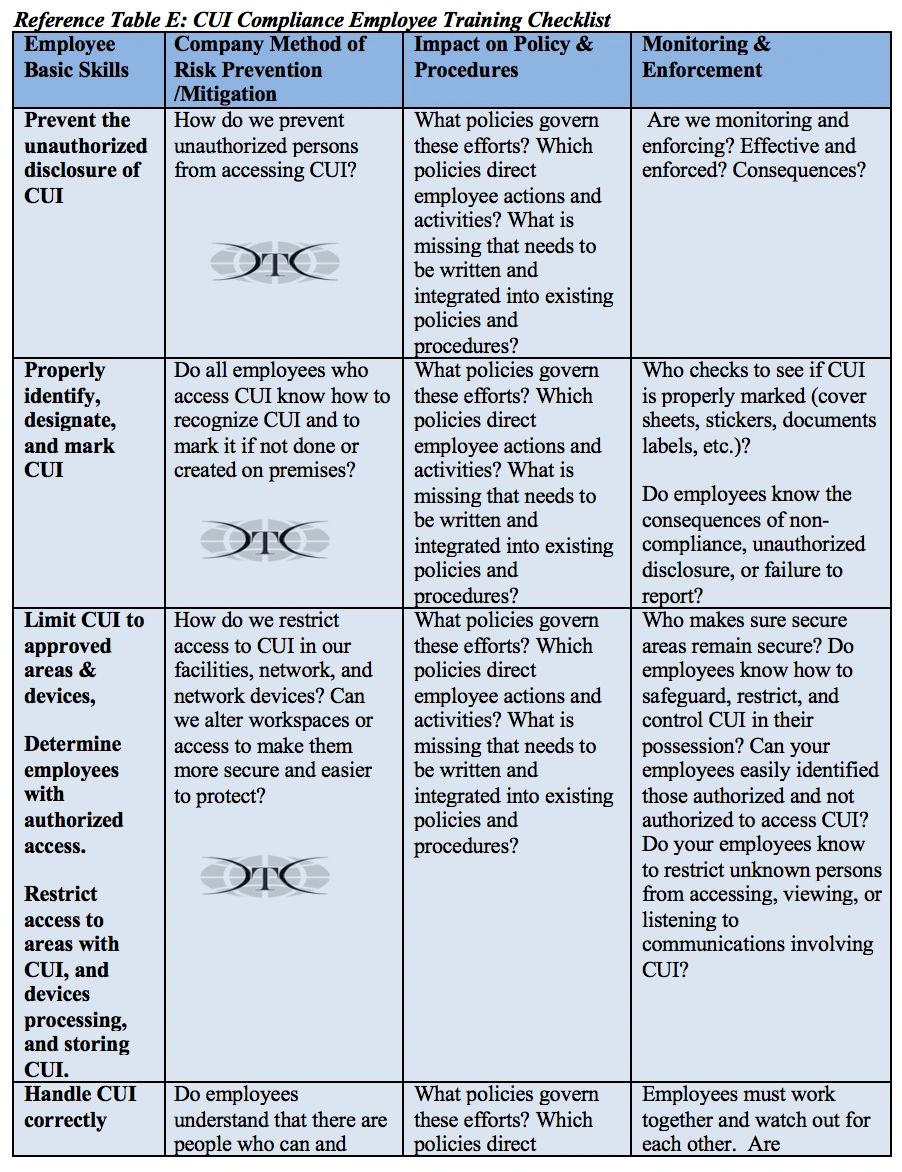
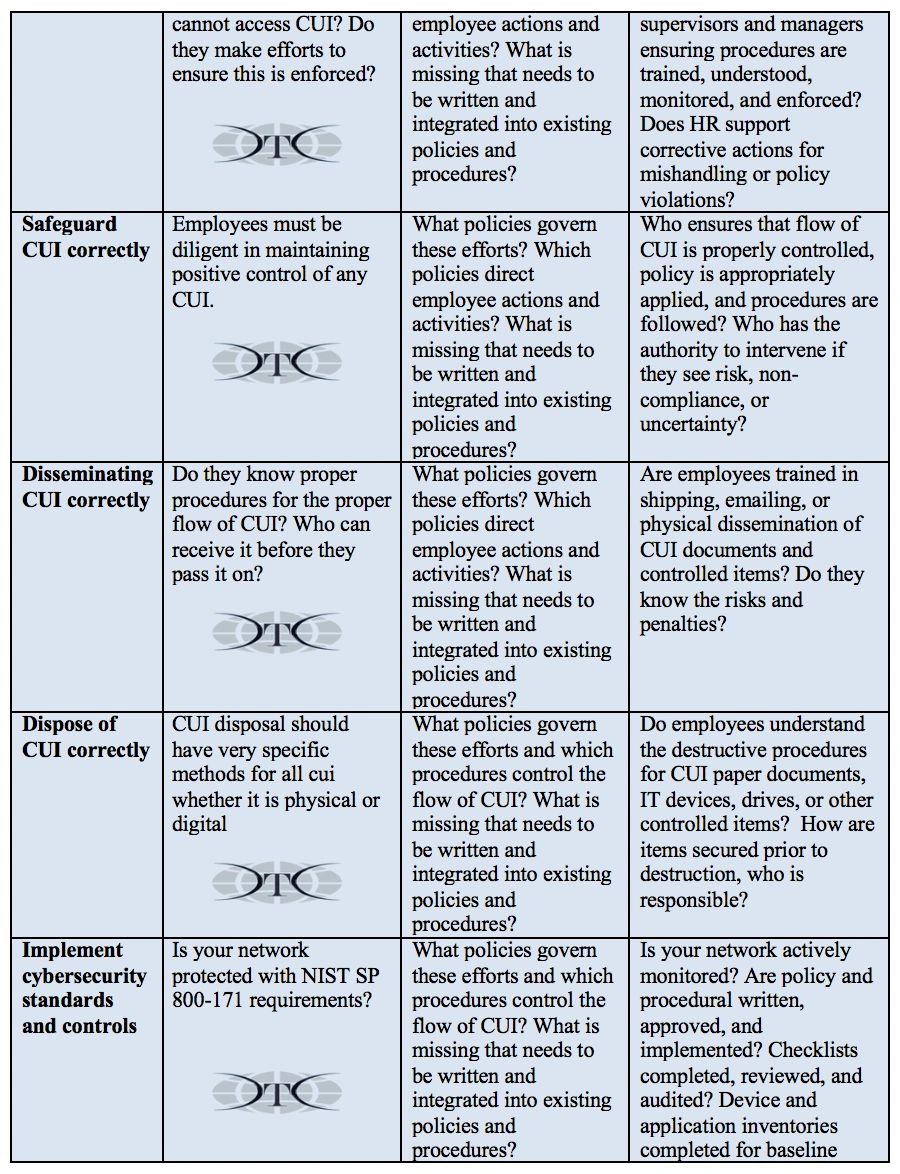
There are several focus areas for training that are required for organizations to maintain DFARS compliance to perform work as a DoD contractor. This involves all employees in the organization handling CUI. The untrained employee is a source of considerable risk. CUI risk awareness training teaches and reinforces the basic responsibilities regarding protection and reporting of security incidents. Safeguarding CUI starts with employees knowing CUI flows through their department.
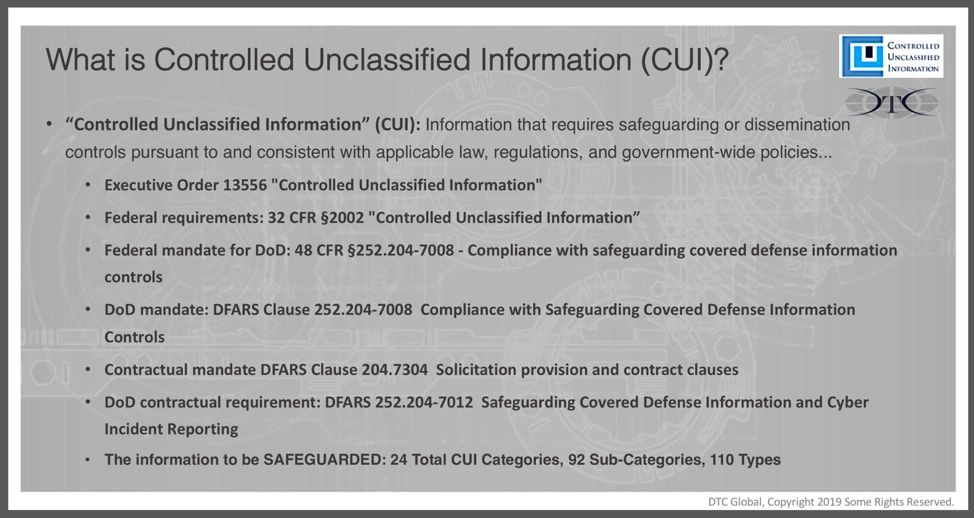
Recognize CUI when you see it.
Prime Contractors generally identify ANY DRAWING or SPECIFICATION as restricted technical data or Controlled Technical Information (CTI). CTI is a specified category of CUI. Examples of forms of restricted technical information include research and engineering data, engineering drawings, and associated lists, specifications, standards, process sheets, manuals, technical reports, technical orders, catalog-item identifications, data sets, studies and analyses and related information, and computer software executable code and source code. The physical representation of that restricted technical information as machined parts, is likely CUI.
An important distinction is CUI isn’t publicly available. If the technical information is publicly available, it’s doesn’t likely qualify as CUI.
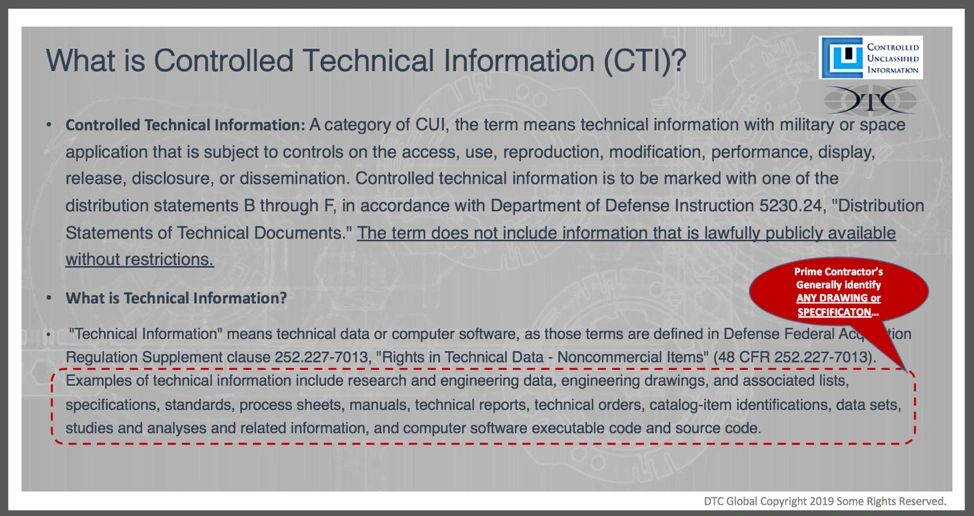
CUI and specified categories of CUI, present challenges on the manufacturing floor or in the production process in the form of physical documents, as components or parts, and often across the entire corporate enterprise when in electronic form. If the document is CUI and not marked, an employee must know how to identify, designate, and mark it properly. In addition, if employees are in possession of CUI they must know how to protect media, document, or controlled items from unauthorized disclosure. Employees need to understand how to appropriately restrict access to CUI by using document covers, properly marking CUI, properly labeling electronic equipment, or lockable storage containers, use screen locks, or other methods such as securing removable media devices in their absence. CUI Marking and labeling is discussed is detail HERE.
There are several critical requirements that set the benchmark for CUI training. Those basic responsibilities are detailed in a Reference Table A. The most critical requirement for building an effective and compliant CUI training program, employee by employee is:
· 32CFR §2002.16 Accessing and Disseminating (a)(4) states, “To disseminate CUI to a non-executive branch entity, authorized holders must reasonably expect that all intended recipients are authorized to receive the CUI and have a basic understanding of how to handle it.”


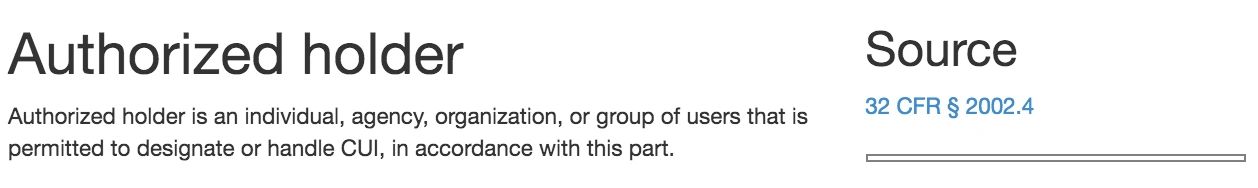
Who are “Authorized Holders” of CUI?
In order to fully understand the areas an employee needs the basic understanding described in 32CFR §2002.16(a)(4), we need to better understand the definitions of “authorized holders” and “handling”. Under the conditions stated in 32CFR §2002.16(a)(1) your company and your employees are qualified to access CUI as “authorized holders” of CUI, when they access and handle CUI for a lawful purpose, and for furthering the Government’s purpose (that means doing the work that is contracted). Your employees are qualified by their purpose for accessing CUI, and not their employee status alone. As “authorized holders”, your employees must abide by the requirements detailed in the Reference Tables, and refrain from doing things that are prohibited in order to properly safeguard and handle CUI.
Understanding Authorized Holders Basic Responsibilities.
Below is a brief detail of the corporate organizations and their employee’s shared basic responsibilities as authorized holders of CUI.
· Authorized holders must comply with 32CFR §2002, the CUI registry, agency policies, and contract terms and conditions. Certain categories of CUI, such as Export Controlled information (EXPT), such as ITAR or EAR technical information or controlled items are handled, these categories have specific requirements identified in specific laws, regulations, and Government-wide policies. Those too must be followed.
Authorized holders of CUI information that includes Export Controlled (EXPT) information are governed by DoD requirements AND additional requirements under the Department of State (ITAR) or Department of Commerce (EAR).
· Per 32CFR §2002, “Authorized holders must be trained to take reasonable precautions to guard against unauthorized disclosure.
- Establish controlled environments.
- Reasonably ensure that unauthorized individuals cannot access or observe CUI, or overhear conversations discussing CUI.
- Keep CUI under the authorized holder‘s direct control or protect it with at least one physical barrier, and reasonably ensure that the authorized holder or the physical barrier protects the CUI from unauthorized access or observation when outside a controlled environment.
- Protect the confidentiality of CUI that agencies or authorized holders process, store, or transmit on Federal information systems in accordance with the applicable security requirements and controls established…. Which for non-government Federal contractors (all agencies) means implementing the requirements and controls described in NIST SP 800-171.
- Authorized holders must reasonably expect that all intended recipients are authorized to receive the CUI and have a basic understanding of how to handle it.
- Before disseminating CUI, authorized holders must reasonably expect that all intended recipients have a lawful Government purpose to receive the CUI. Authorized holders may then disseminate the CUI by any method that meets the safeguarding requirements and the CUI Registry…” See Reference Table A.
CUI Handling Responsibilities = Training Requirements, Content, and Frequency.
Companies receiving, disseminating, archiving, or creating CUI must understand the basic responsibilities, understand risk areas, and communicate handling guidance to your employees in the context of your company’s business model, workflow, and business technologies. Governing policies and procedures must be written to address their basic responsibilities, guide employee activities and decisions, provide direction consistent with the work environment and supporting technologies, and provide authority and means for monitoring, enforcement, reporting and corrective actions. Beware of template policies because they are often not compliant, lack sufficient detail, and poorly understood by employees responsible for enforcing them. Training is essential to integrating CUI-impacted policies and procedures in a manner sufficient for employees to sustain a CUI compliant work environment.
The fundamental component to a company’s successful CUI compliance program, however big or small, is that employees need to be qualified, authorized, and trained prior to receiving CUI.
Training requirements need to focus on the basic understanding of handling requirements, and also include other specific requirements identified within 32CFR §2002, NIST SP 800-171. Employers need to monitor the guidance from the National Archives, Information Security Oversight Office, and current and emerging changes in Department of Defense policy or other training requirements identified with laws, regulations, and applicable Federal agencies. Training is the critical element required to ensure qualified and authorized employees have the required understanding of how to handle, safeguard, and share CUI data in accordance with the Federal requirements. The training content is outlined in Reference Table B below, and specifically addressed in 32CFR, part 2002.14 Safeguarding sections (a)(4), (b)(1)(2), (c)(1)(2)(3)(4), (g), (g)(2) and 32CFR, part 2002.16 Accessing and Disseminating (c)(1).
These requirements apply to all non-Federal organizations (private companies) and they must also meet NIST SP 800-171 minimum standards for protecting both CUI Basic and CUI Specified categories. An employee’s knowledge of governing corporate CUI policies and appropriate procedures is critical to meeting safeguarding requirements. They guide, restrict, and reinforce employee decisions and actions as authorized holders of CUI.
In order to meet all DFARS requirements, employees will need to be trained at orientation so they can handle CUI, and then annual training sustains employees’ knowledge, skills, and abilities. A best practice would be for new employees to fall into the same annual cycle with other employees. This may mean they receive it again before the anniversary of their hire date, but then all employees stay on the same training schedule, making it easier to manage, track, and remain compliant. Some categories of CUI, such as Export Control Information (EXPT) specifically require additional annual training on EXPT specific requirements and training appropriate to their role and responsibilities.
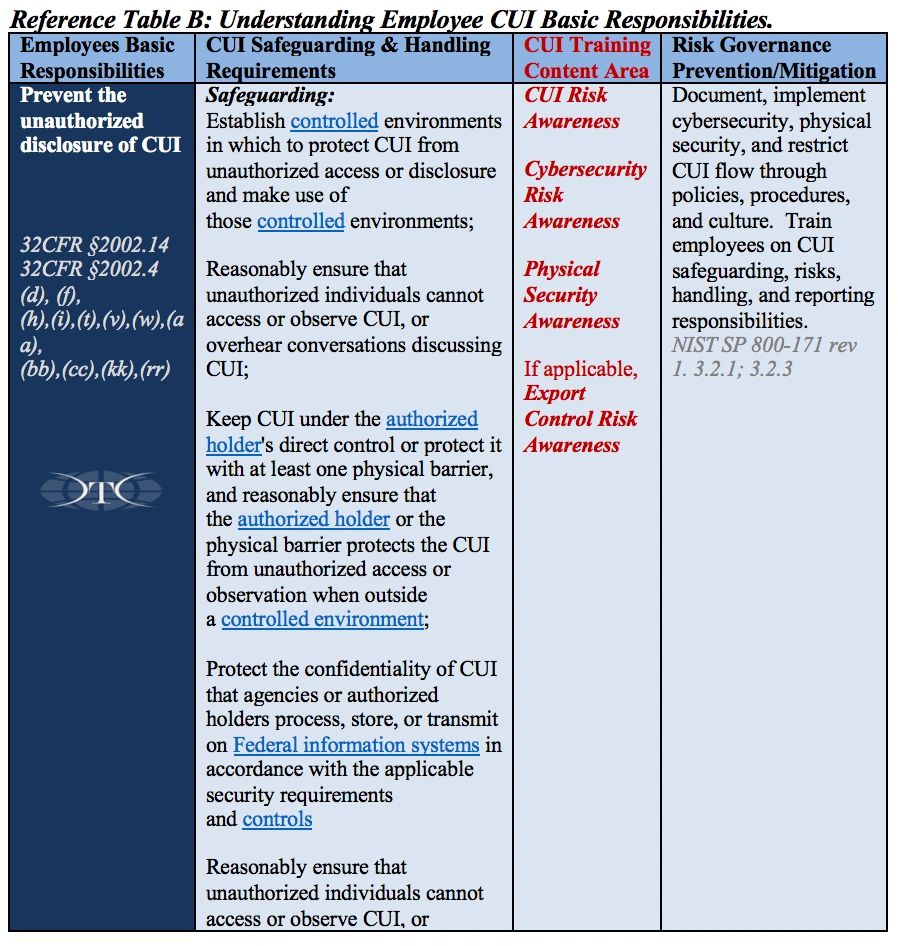
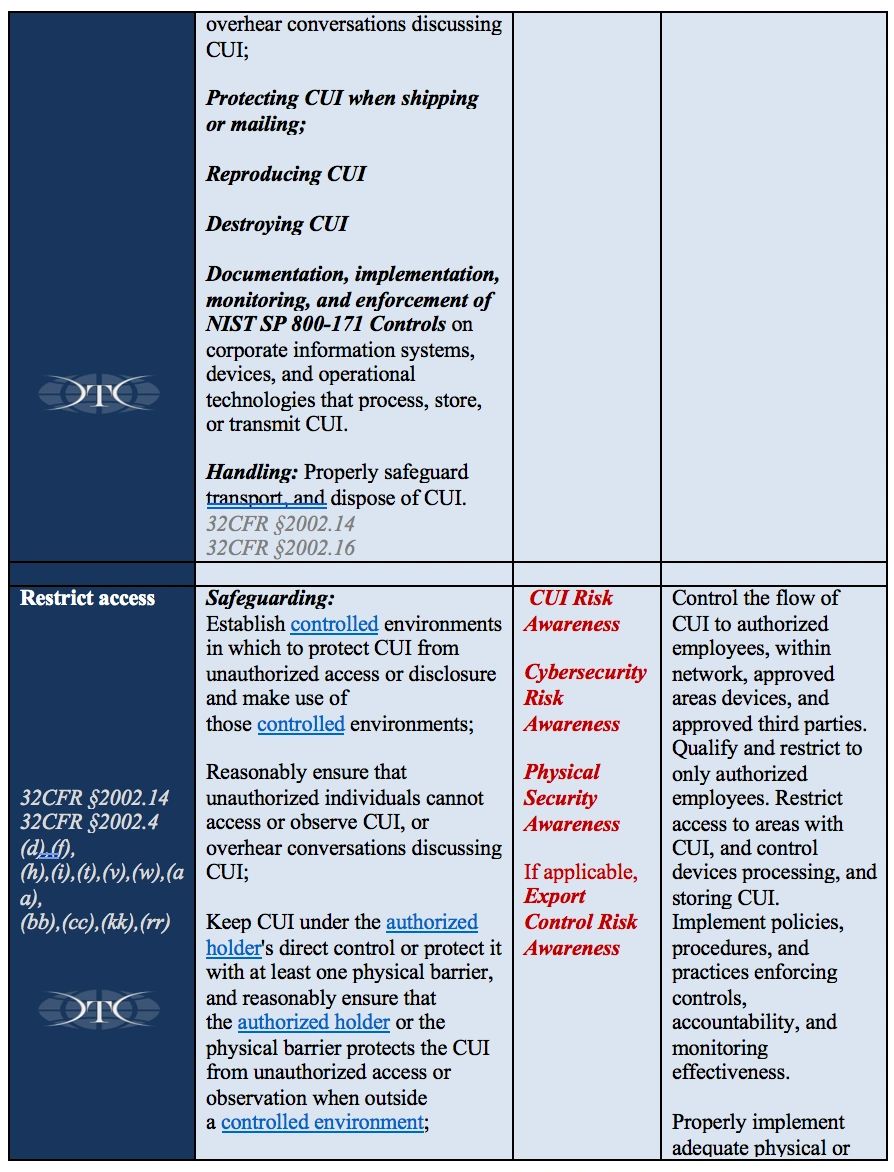
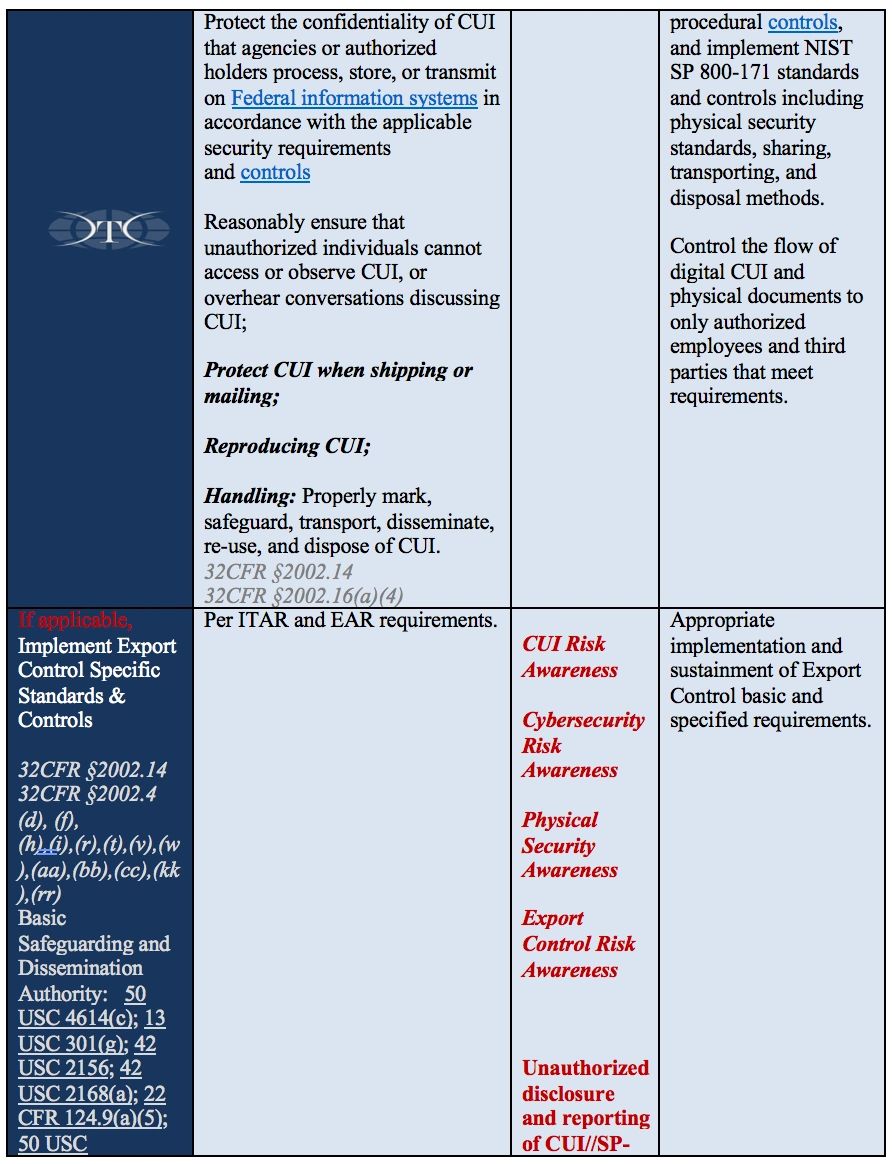
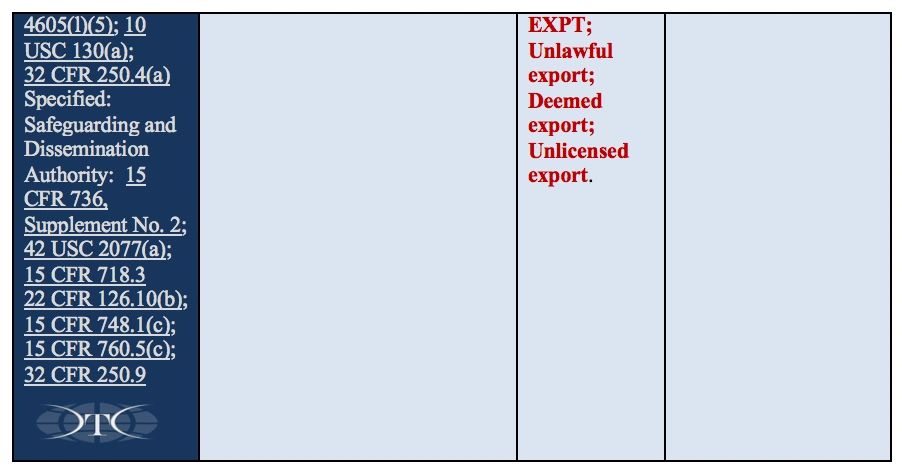
Why do we have to train employees in these four specific areas in order to fulfill the “basic responsibilities and handling requirements” DFARS, CUI, and NIST 800-171 requirements?
Smart employers understand and manage risk to prevent all sorts of bad things from happening to their company. Critical risk areas include employees, products, customers, sensitive data, and quality. DoD’s intensive focus on safeguarding CUI with NIST cybersecurity requirements creates a trifecta of non-compliance risk when companies are impacted also by existing export control (ITAR/EAR) requirements. If companies manage their risks effectively, they can stay focused on delivering their products and services, while running a successful business. Companies use policies and procedures to guide and govern employee decisions and actions. Training engages employees to partner with employers to reduce and prevent specific risks through shared responsibility, awareness, and accountability. In order to prevent or reduce risks, employees must be aware of specific controls, limitations, requirements, and the consequences of violating governing policies and procedures. For the breakdown by each of the four areas is below, with specific requirements for Export Controlled information, See Reference Table D at the end of the article.
The Golden Rule of CUI: CUI risks, responsibilities, and training follow the data, WHEREVER the data goes, physically and digitally.
Conclusion.
Cyber security within the Department of Defense (DoD) is front and center on the national stage and one of the most important aspects of this is changing the culture of organizations to get their personnel up to speed. “Blinky Lights” and “Electronic Widgets” are indispensable, but enduring security and sustainable compliance comes from knowledgeable and trained employees who understand their roles and an employer’s expectations for safeguarding, handling CUI in order to sustain DFARS compliance over the long-term.
The possibility of an information network-based breach, inadvertent compromise of CUI, or numerous other mishaps are high risk threats to every company. Needed changes within a company’s culture starts with the CEO and filters down into every employee, consultant, vendor, and subcontractor with network access or in any way involved with CUI as it flows through your business process must be trained. Despite heavy investments, network security technologies have limited capabilities to prevent compromise or other bad things happening and are no substitute for annual role-based training. The opposite, expensive technology investments are optimized by a knowledgeable and well-trained workforce.
Applying “Due Care” standards to CUI responsibilities is very important in understanding the value of training to manage risk, steward the national security interest, and meet the expectations within your contractual, legal, and ethical responsibilities for safeguarding and handling CUI data, documents, and controlled items. Safeguarding CUI is good for business and good for our country. Training is a win, win, win for everyone.

REFERENCE TABLES C,D,E,F



Recent Comments