Most people generally think about compliance as a necessary evil. Most executives see IT as a cost center that seems to push their corporate overhead costs higher and higher each year. Cybersecurity is on the list of topics that’s keeps CEO’s up at night, but that list is long and dominated by the tyranny of the urgent. No CEO wants a breach of their intellectual property, financial data, or their customer’s sensitive technical data to be exposed to malicious actors. Over the past 15 years of experience within the intelligence world, and having led my first cybersecurity special capabilities program in 2006 to detect and identify foreign intelligence efforts to compromise a Coalition Operations Center network responsible for directing combat operations in two theaters of war… since then the amount of data, dollars, lives, jobs, and businesses lost to cybersecurity compromises is estimated to be a cost of $6-7 Trillion dollars to the U.S. and global economy by 2021. AT&T’s “CEO’s Guide to Data Security” correctly puts that number in perspective. “This represents the greatest transfer of economic wealth in history [of mankind], risks the incentives for innovation and investment, and will be more profitable than the global trade of all major illegal drugs combined.”

Cybersecurity’s Achilles Heel, Behavior Not Technology. Cybersecurity Ventures estimates the global spend on cybersecurity between 2017-2021 will be over $1 Trillion. So what do we do about a $1 Trillion cyber defense spend on technologies chasing a $6 Trillion cyber crime spree. We look at the cyber attack threat vectors, methods of attack, and sources of breaches. The ugly reality is the failure of the next, next, next generation firewall technology that it isn’t capable of closing the gap on the majority of the user-behavior (created) vulnerabilities. Combine email, phishing, compromised credentials, employee error, insider threats, poor cyber hygiene, and about 85-90% or more of breaches are cause by employees. The challenge is human behavior and the risk created by network users.
Matthew Moynhan’s says in his article, “How Not to Waste a Trillion Dollars on Cybersecurity”,
“Today’s sophisticated threat landscape is a rich, multifaceted organizational challenge that requires insight on how data is used across myriad business functions. Shifting the focus to understanding the behavior patterns of people and their interactions with technology provides clarity in regard to who is using sensitive data, why and from where.
Having a baseline for behavior, a digital rhythm or routine, can help security and business leaders better manage risk. If an employee is working normally on the job, IT can get out of the way. But if the behavior is inconsistent with the organization’s mission, IT can recognize the risk and quickly respond with coaching or stronger enforcement policies. Context matters. Security teams that only focus on securing computers and servers will miss the broader perspective and the signs of an incident or data breach until months after it happened.”
NIST 800-171 establishes a security baseline for technology and user behavior in how we protect the networks and devices that contain certain types of data our adversaries desire. Over 20 years at the tip of the spear in special operations, intelligence, and technology has taught me a valuable lesson that winning the fight is always about the fundamentals. Technology is most effective when we master fundamentals and technology enhances our capabilities, and least effective when we fail at the fundamentals, and technology is expected to make up the difference. The US Defense Industry is trying to run their businesses, keep America, and their families safe. Well-intentioned, but the bitter truth consistently allows attackers to prevail, cybersecurity has been fundamentally lacking for over a decade and it’s cost us, our families, and children, and our future grandchildren dearly. The spill over benefits from NIST 800-171 compliance could be that by establishing a security baseline for technology and user behavior in portions of US Industry, we see a net reduction invulnerability and make the attackers work much harder or choose softer targets in other business sectors. Will NIST 800-171 compliance stop a determined state-sponsored hacker group, of course not, but maybe we can stop leaving the keys to the gates of Fort Knox containing US Defense Industry Intellectual Property under the virtual front door mat. We can also help reduce the vulnerability of other types of business data, financial loss, and other types of breaches and areas of compromise that malicious actors use to fund their mayhem. The largest transfer of wealth in the history of mankind, requires leadership. Leaders establish and enforce standards to bring order to chaos, so we can start addressing this serious challenge. It’s a start.
US Manufacturing at Risk. Cybersecurity industry reports from Verizon and Deloitte can help CEO’s and the Board realize that NIST 800 isn’t about compliance for compliance sake. There’s a legitimate business and national security interest at stake. US manufacturing, and especially the US Defense Industrial Base is at great risk. Malicious actors choose “soft targets” because there is a much higher rate of success, even if the payoff is smaller.
“Manufacturing executives indicate four of the top 10 cyberthreats facing their organizations are directly attributable to internal employees. These threats include: phishing/pharming, direct abuse of IT systems, errors/omissions, and use of mobile devices. Smaller companies (<$500M in revenue) are more exposed to direct employee threats while mid-size companies ($500M–$5B in revenue) are more concerned with intellectual property theft and large companies (>$5B in revenue) report their largest cyber risk concern focuses on phishing and pharming threats, which most often target financial gain or intellectual property.” Deloitte, “US Cyber Risk in Advance Manufacturing.”
This gap in protection created by internal employees is because of the lack of consistency in cybersecurity controls, requirements, missing or inconsistent IT security policies and lack of enforcement. A profound lack of employee training and awareness on cyber risks, threat, and methods of attack, and inconsistent standards and practices by employees regarding sensitive data/devices, all contribute to the behaviors creating advantage to the attackers who walk through the profound gaps in the defense that cybersecurity technologies cannot overcome. These are the reasons for NIST 800-171 compliance and the new Cyber Maturity Model Certification (CMMC).
The International Trafficking in Arms Regulations (ITAR) with an army of mandates has tried to safeguard the proliferation of sensitive data. The task is enormous, but failure to pivot the approach to address the convergence of data, data protection, cybersecurity, and technology would be fundamentally flawed. NIST 800-171 standards for safeguarding export control data begins to address this historical weakness in those efforts. Whether state sponsored or not, malicious cyber actors have the advantage, because it’s “easier” to line item the budget to buy new security technologies than to address the root cause of vulnerabilities caused by the lack of standards and enforcement of a security baseline for networks, technologies, and user behavior.
Prime contractors are responsible for their suppliers. With NIST 800-171 compliance requirements, that all changes and the enforcement is ramping up quickly with increased standards and third party certification in 2020. Better to begin the path towards compliance now, be ready to demonstrate your corporate commitment to those efforts now, or companies will find themselves alienated from prime contractors and unable to do business with the Federal Government. Prime contractors are responsible to make sure all their suppliers contractors handling Controlled Unclassified Information are compliant. The day is approaching very quickly, that if a company is not compliant, primes will have no choice to seek out other NIST 800-171 compliant suppliers, or lose the contract.
Controlling the flow of CUI. One of the major misconceptions about NIST 800-171 compliance is most people think it’s just referring to just the IT Network, but it follows the Controlled Unclassified Information (CUI) in any form it takes throughout the business processes…documents, prints, drawings, products, and the physical spaces within the facility, inventory, and impacts the employee behavior and procedures that involve CUI data. The raised security standards with CUI, the network, and devices impacted by NIST 800-171, all creates an opportunity to reduce the vulnerability of the entire company.
NIST 800-171 compliance can fuel the capture of market share. The smart play to is get compliant and engage your prime contractor to capture the business of your competitors who are not compliant. RIGHT NOW. This is a very clear competitive differentiator that could amount to a major influx of sales and market share over the next 12-24 months. This is also an effective way to discount the price of the acquisition of a company as you target defense companies for purchase. The money saved on the acquisition price can fund the path towards compliance.
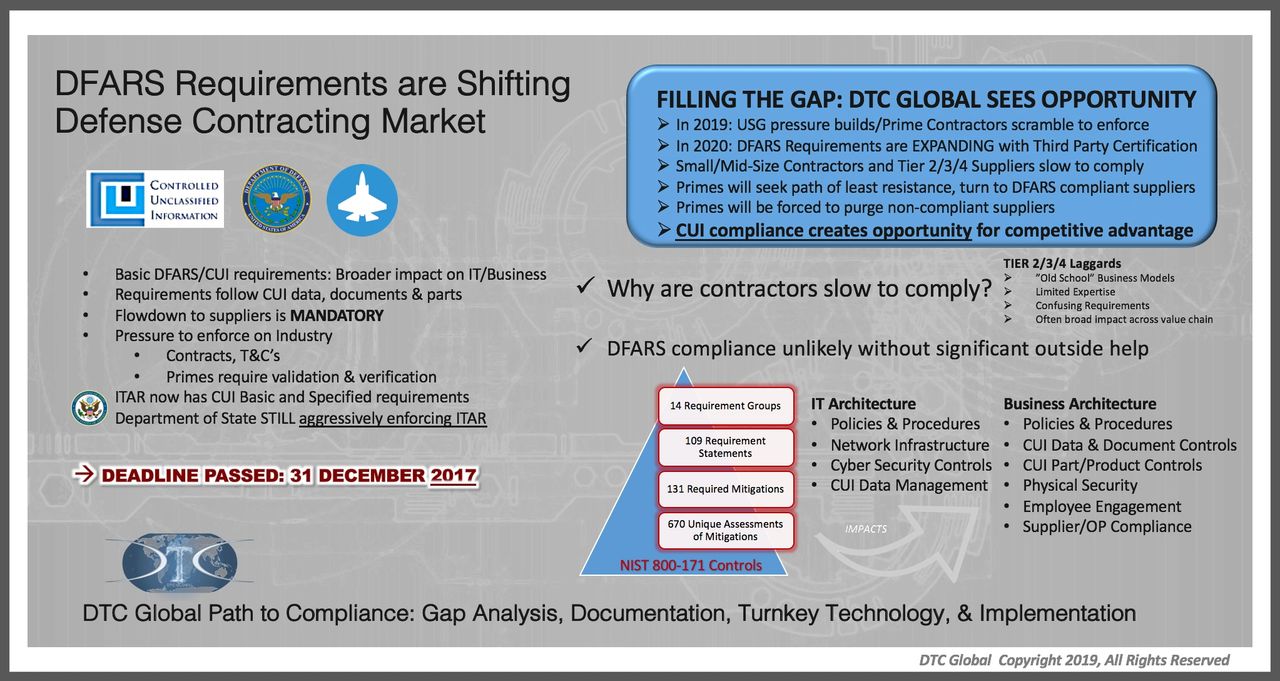
Engage the board to develop a business-driven NIST 800-171 compliance program. Deloitte reports, the three greatest organizational barriers to cybersecurity are increasingly sophisticated threat, lack of will to do the heavy lifting to change without being forced, and lack of funding. Yet, only 52% of executives in the manufacturing industry surveyed said they were confident their assets were protected from external threats, and 48% lacked adequate funding. The largest threat that manufacturers see is theft of intellectual property. Within the Defense Industrial Base, CUI as Controlled Technical Information is the de facto intellectual property of our national defense.
Intellectual Property Protection. Last year 39% of manufacturers experienced a cyberattack. Out of those companies who experienced an attack the financial losses, 46% of them lost between $500k and $10 million, and 2% lost over $10 million. Source
The Cyber Maturity Model Certification (CMMC) will significantly change the landscape for government in Q4 2019 and 2020. Third party certification will expose those companies who have elected to ignore or delay the implementation of the NIST rules two years past the deadline, and could be in danger of losing their contracts or status as a supplier to those competitors who committed to NIST 800-171 earlier.
Be Secure – Begin the path to compliance by conducting a detailed risk and security assessment looking at the IT enterprise AND the business processes that are impacted by NIST 800-171 requirements. Take the opportunity to integrate operational efficiencies throughout your value chain as you align requirements with reality in employees day to day activities. Revise your company policies governing IT, sensitive data management, AND the work instructions impacted by NIST requirements and move forward aggressively to capture the business late adopters may lose.
Be Vigilant – Train your employees to understand the methods most likely used by cyber attackers to result in a breach and HOW THEIR BEHAVIOR ALL THE DIFFERENCE IN YOUR DEFENSE. Reinforce what they learn and reward employee vigilance. Monitor systems, applications, people, and enforce security policies consistently in order to detect anomalies and incidents more effectively. Enforce strong cyber hygiene practices in policies, procedures, and performance evaluations. Use NIST 800-171 as an opportunity build a security minded corporate culture.
Be Resilient– Be prepared for incidents, ensure your incident response capability is more than a written procedure- practiced, capable, and ready. Use network operations and security metrics to provide insights and improve outcomes beyond IT. Capture lessons learned on security incidents, improve security controls, revise policies, procedures, and get back to business as quickly as possible.
Recent Comments